BUUCTF-Reverse
红帽杯
[2019红帽杯]Snake
ACTF新生赛
[ACTF新生赛2020]easyre
upx -d脱壳
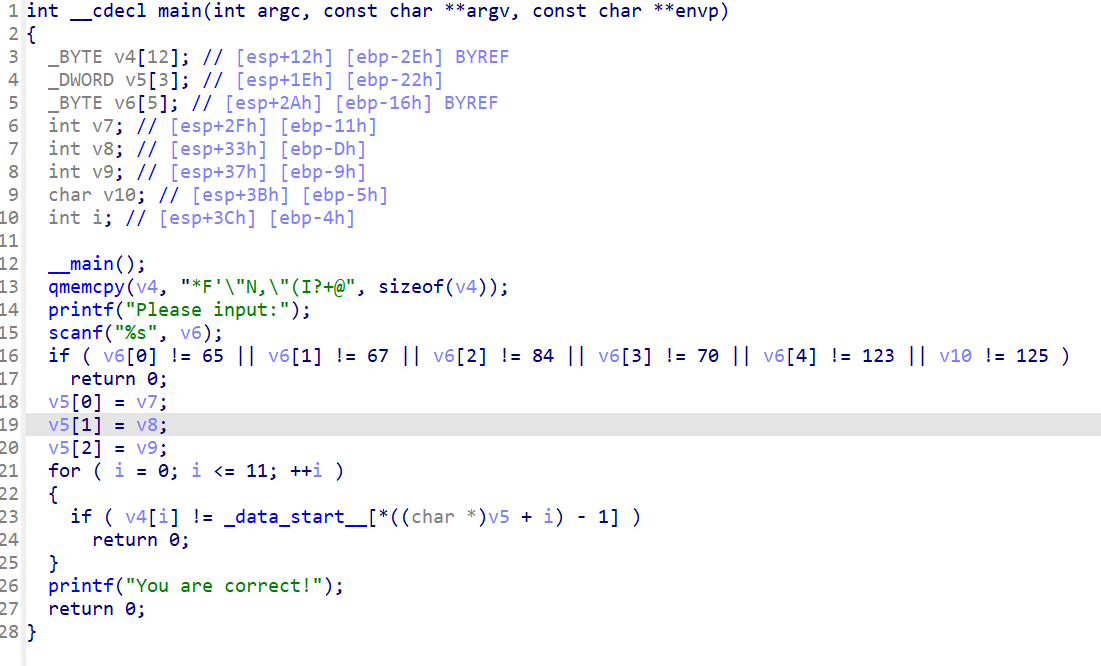
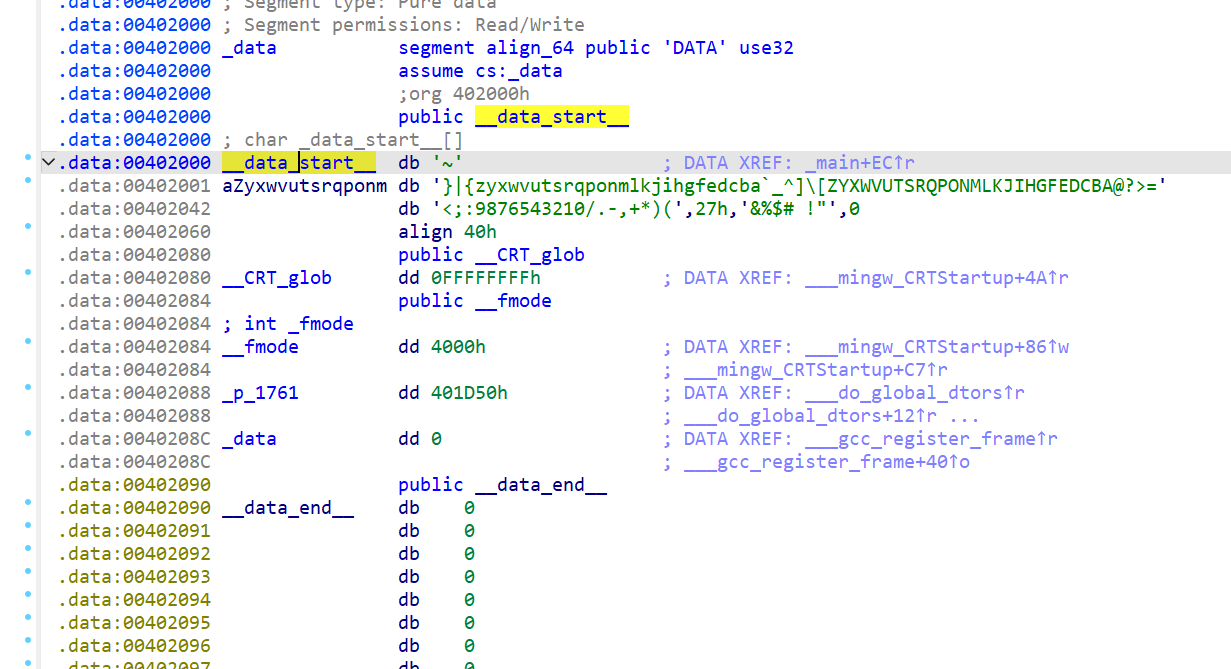
IDA打开发现只有一个简单的加密,加密后为v4,即*F'\"N,\"(I?+@
shift+E提取数据,编写python解密
1 | v4 = "*F'\"N,\"(I?+@" |
[ACTF新生赛2020]Oruga
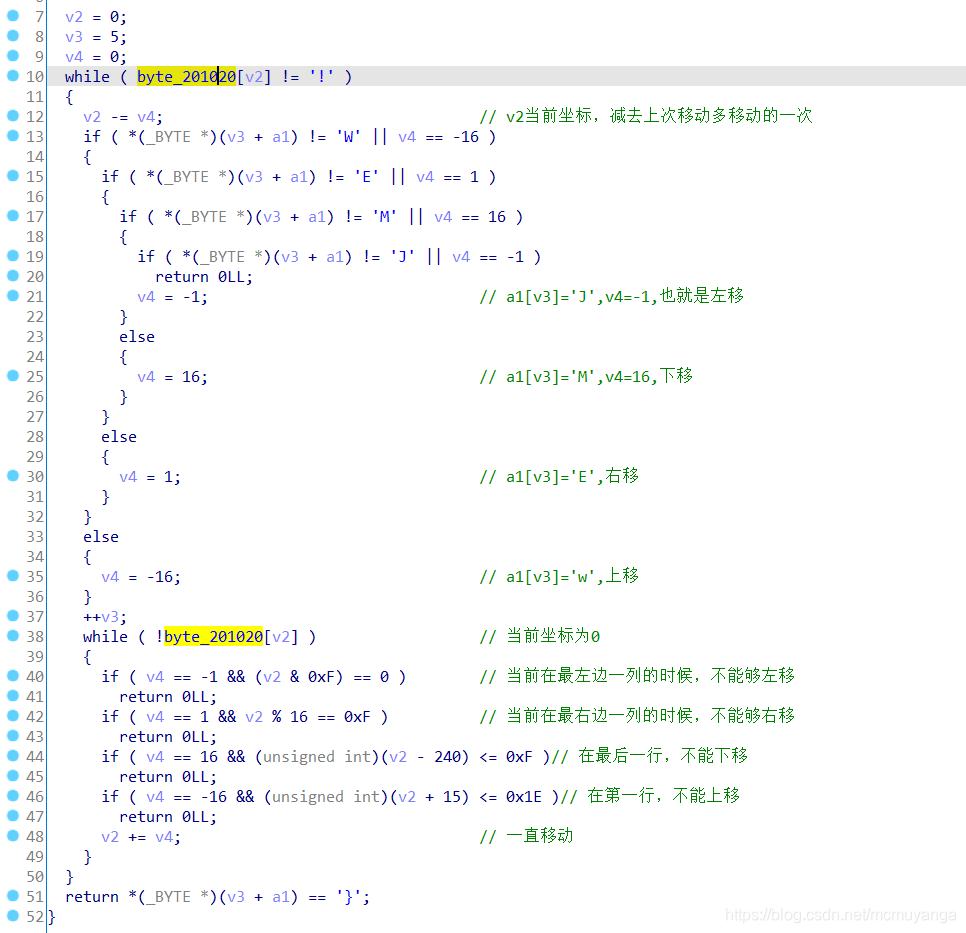
迷宫题,与常规迷宫有点不一样
- 迷宫,终点
!,迷宫在byte_201020
- 在
byte_201020[]按shift+E提取迷宫,变为迷宫,指定行、列
1 | unsigned char ida_chars_byte_201020[] = |
- 同一障碍为
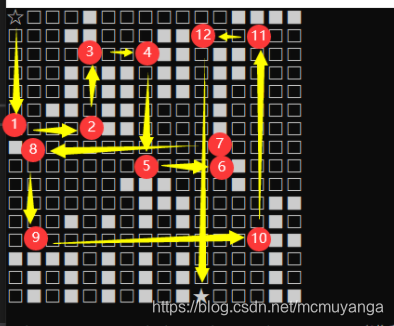
#以便后续脚本,当后来发现这不是通常的迷宫,用bfs算法走的路径是错的,关键在v2 += v4这表示一直移动,所以移动应该是按下面图片来走
1 | maze_str = (" # #### ## OO OO PP L OO OO PP L OO OO P LL OO P OO P # # MMM # MMM EE 0 M M M E EETTTI M M M E T I M M M E T I M M M! EE") |
向下移动:M
向左移动:J
向上移动:E
向右移动:W
flag{MEWEMEWJMEWJM}
- 找的网图大概这样走
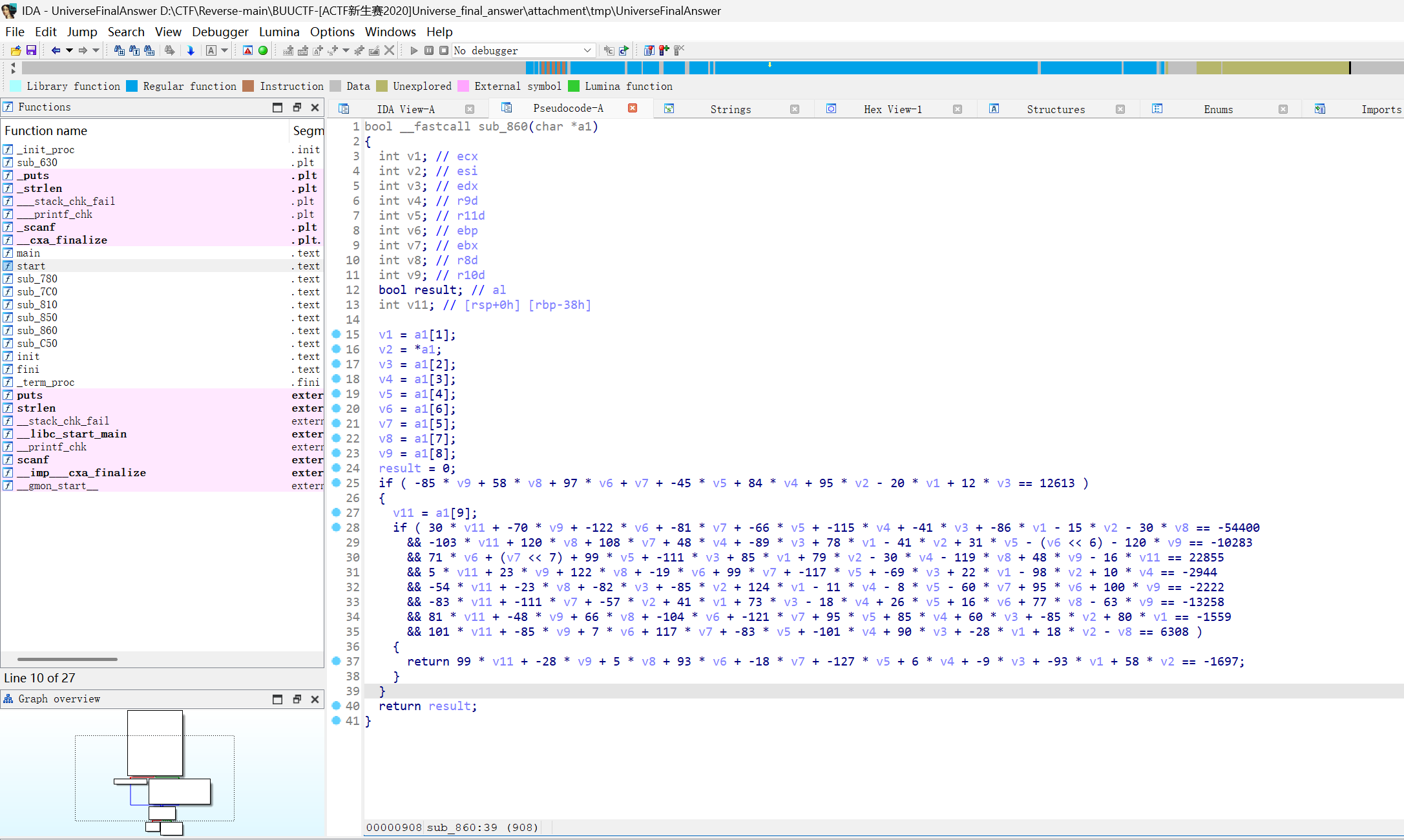
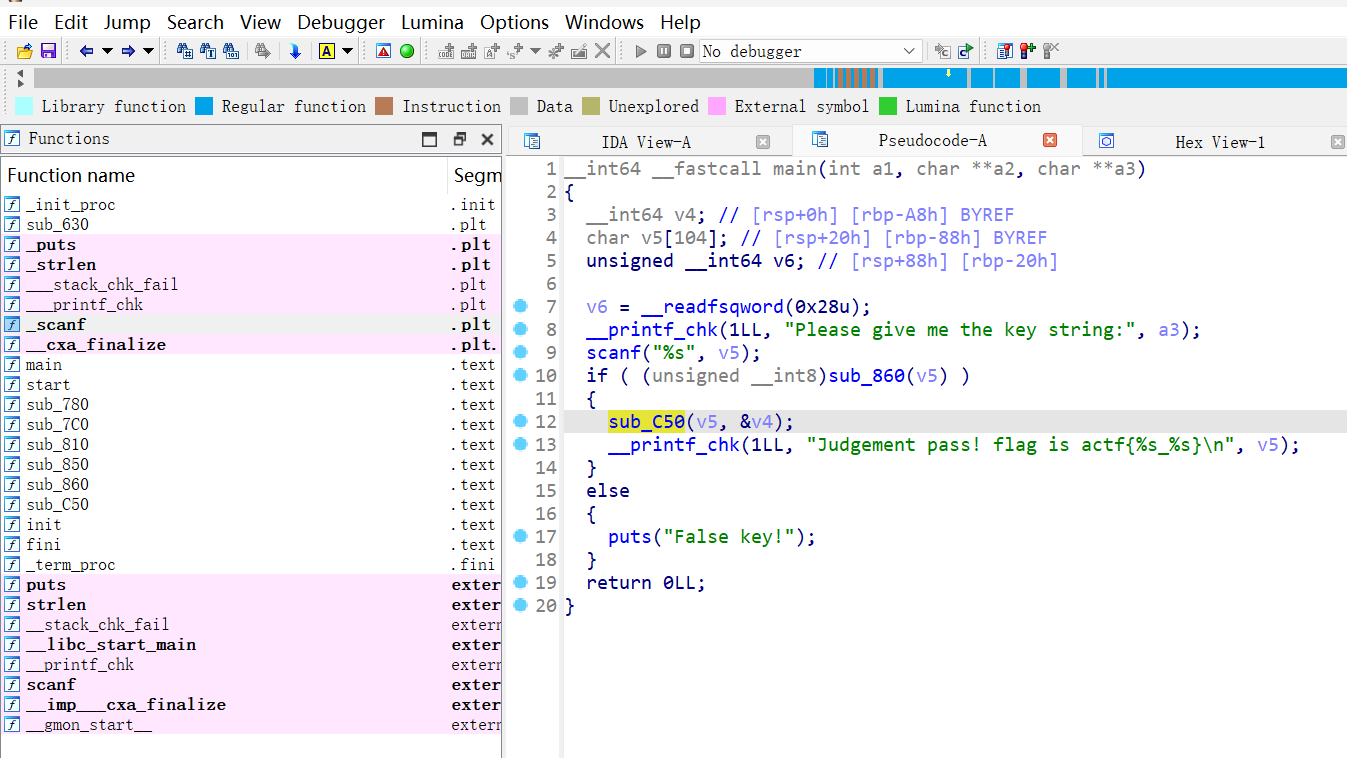
[ACTF新生赛2020]Universe_final_answer
- 64位,无壳,IDA打开
- 用z3处理,根据图中,v1和v2,v6和v7要交换一下
1 | from z3 import * |
- 还有一步
sub_C50,再运行程序输入F0uRTy_7w@,得到F0uRTy_7w@_42
1 | flag{F0uRTy_7w@_42} |
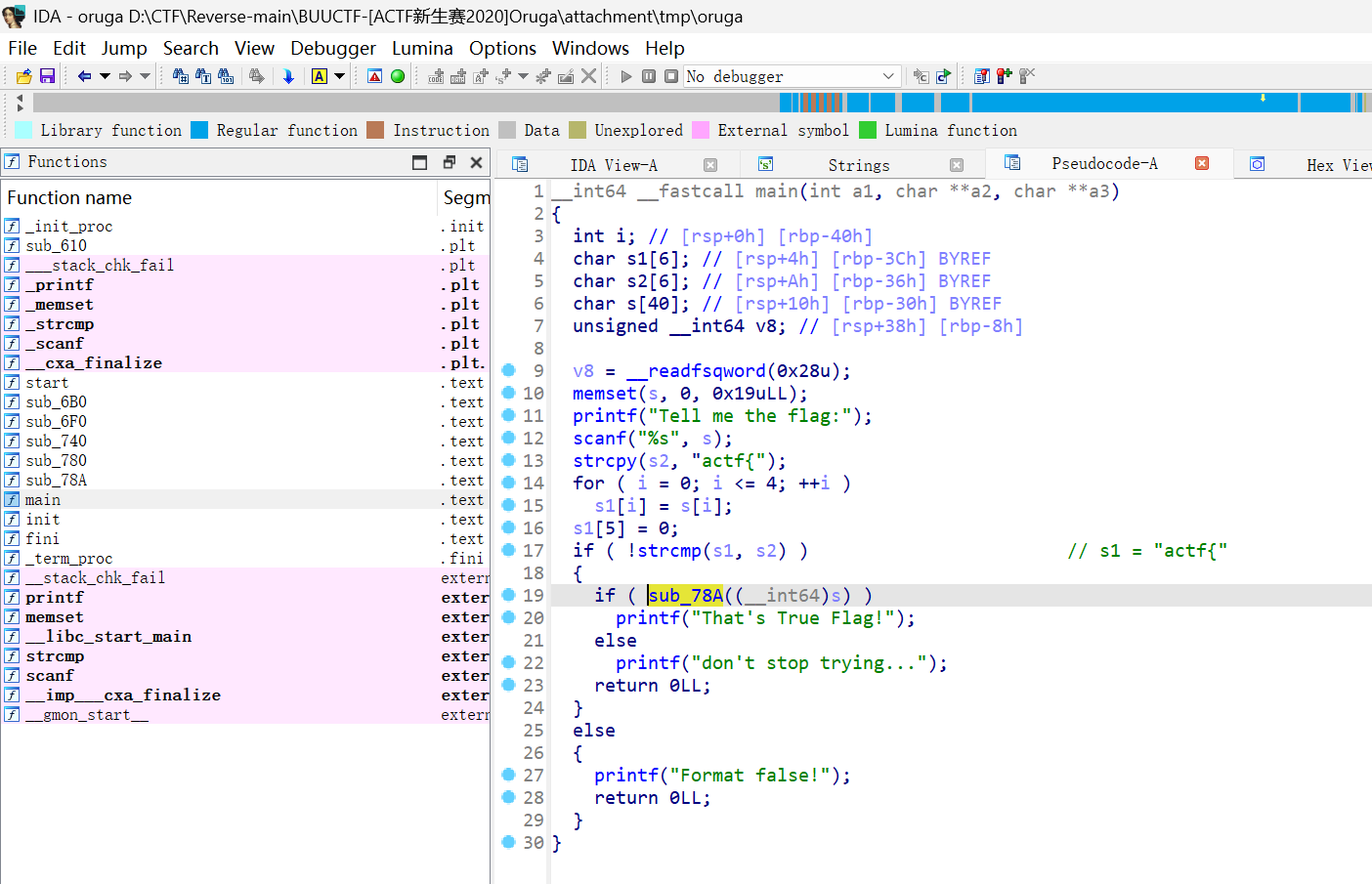
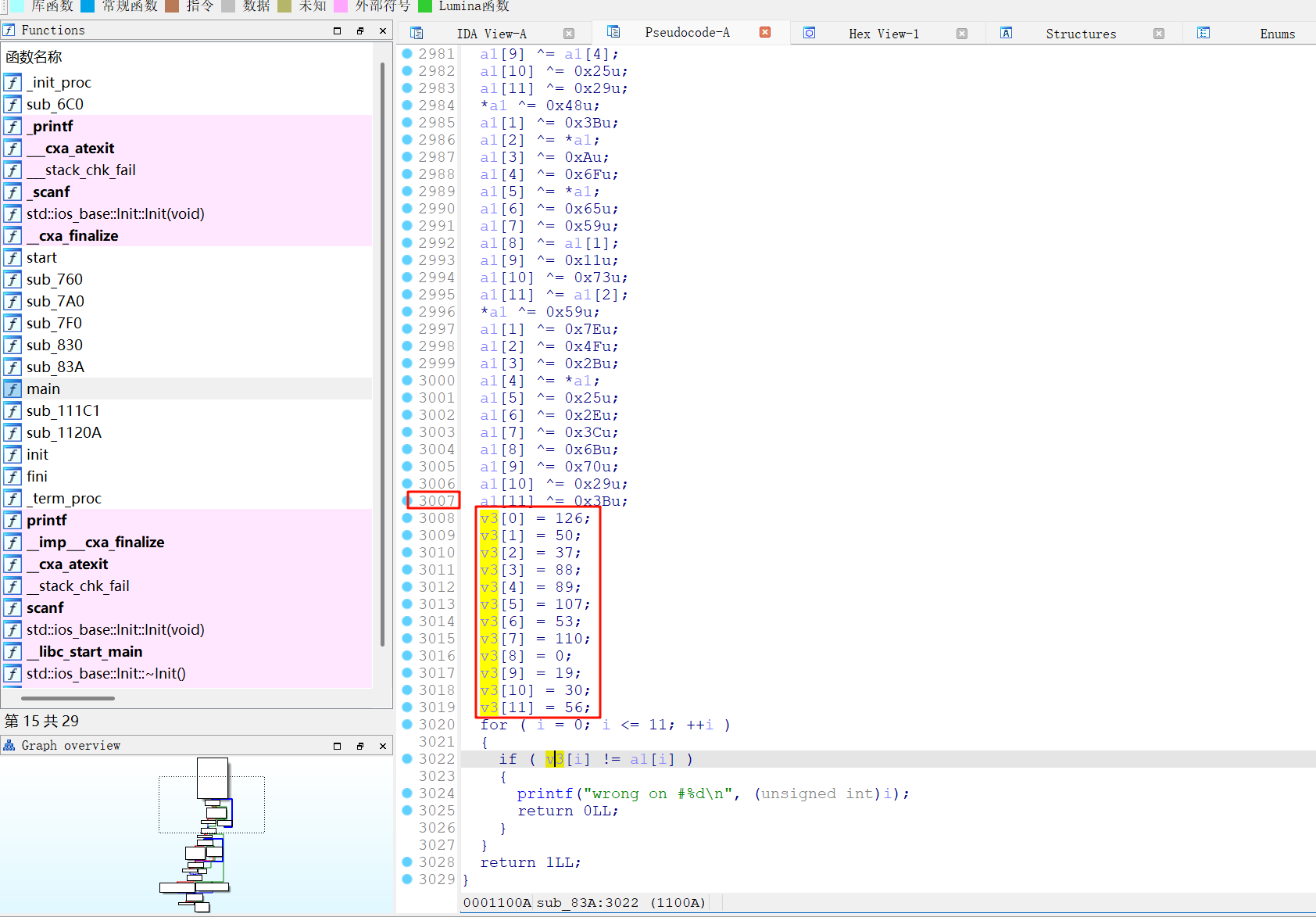
[ACTF新生赛2020]SoulLike
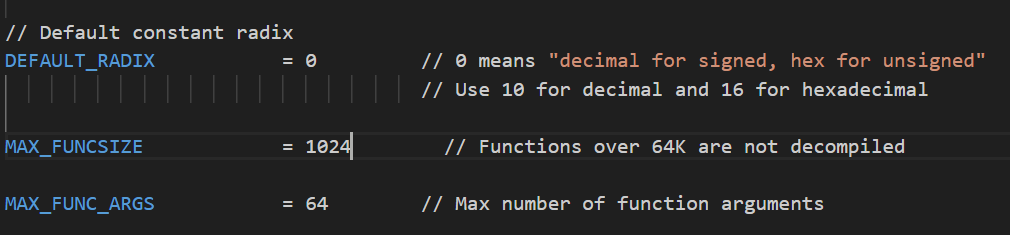
sub_83A显示不出来问题解决方法:找到ida目录中的cfg/hexrays.cfg文件,将其中MAX_FUNCSIZE = 64修改为1024
进行了3000多行的异或操作,然后用异或结果与v3进行对比
flag{b0Nf|Re_LiT!}
找到的三种方法
exp1:暴力破解
1 |
|
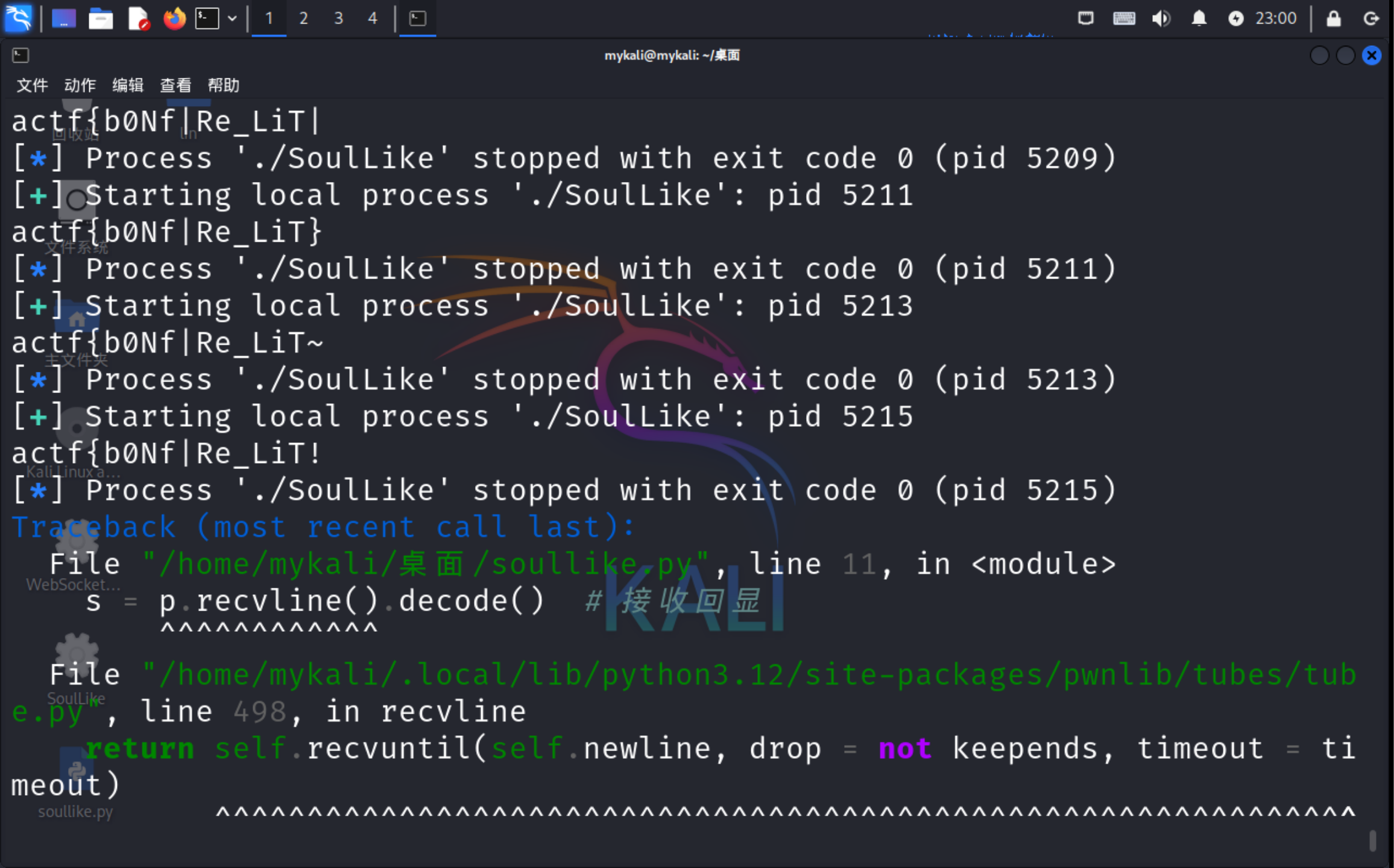
exp2:使用pwntool暴力破解,
1 | from pwn import * |
exp3: 使用angr
angr_ctf——从0学习angr(一):angr简介与核心概念 - Uiharu - 博客园
1 | import angr |
虽然一开始都处理,但现在这三种方法都弄懂了,还是收获满满的
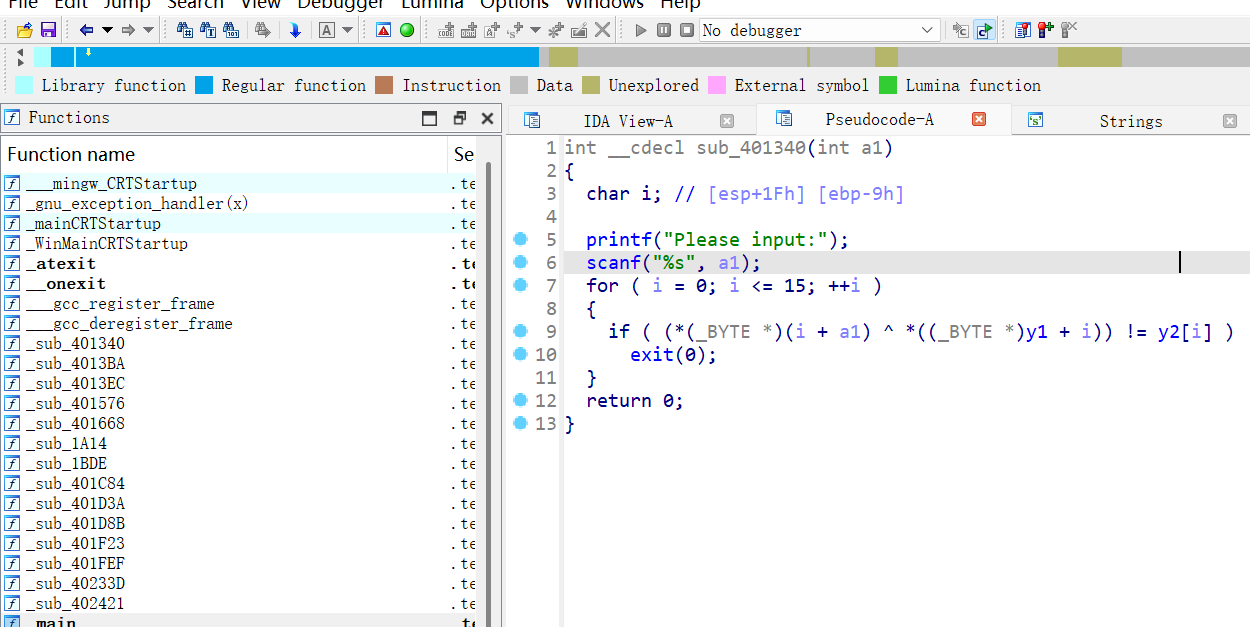
[ACTF新生赛2020]fungame
一个简单的异或
1 | y1 = [ |
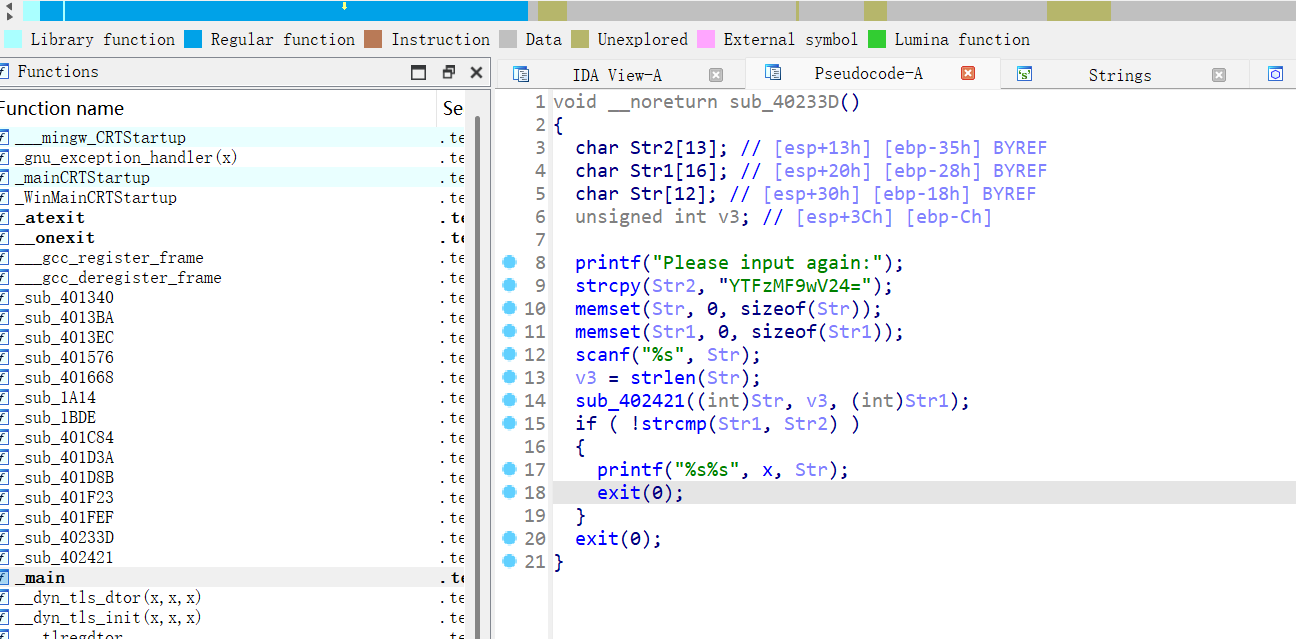
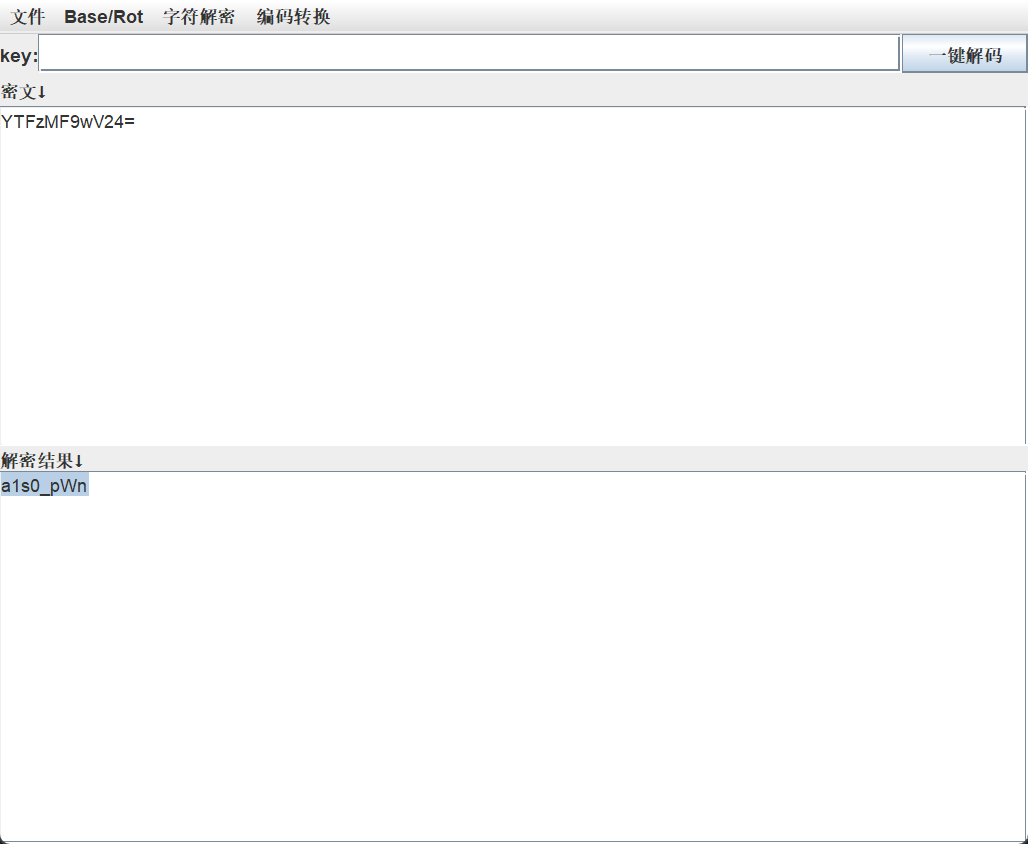
提交然后发现不对,结合在字符串表里看到的please input angin:和base64表,因为运行程序提示输入的是please input,且输错就退出了,所以查看一下please input angin:所在地方
但还是有问题,最后经人提醒才知道,还考了栈溢出的知识,也就是a1s0_pWn的提示
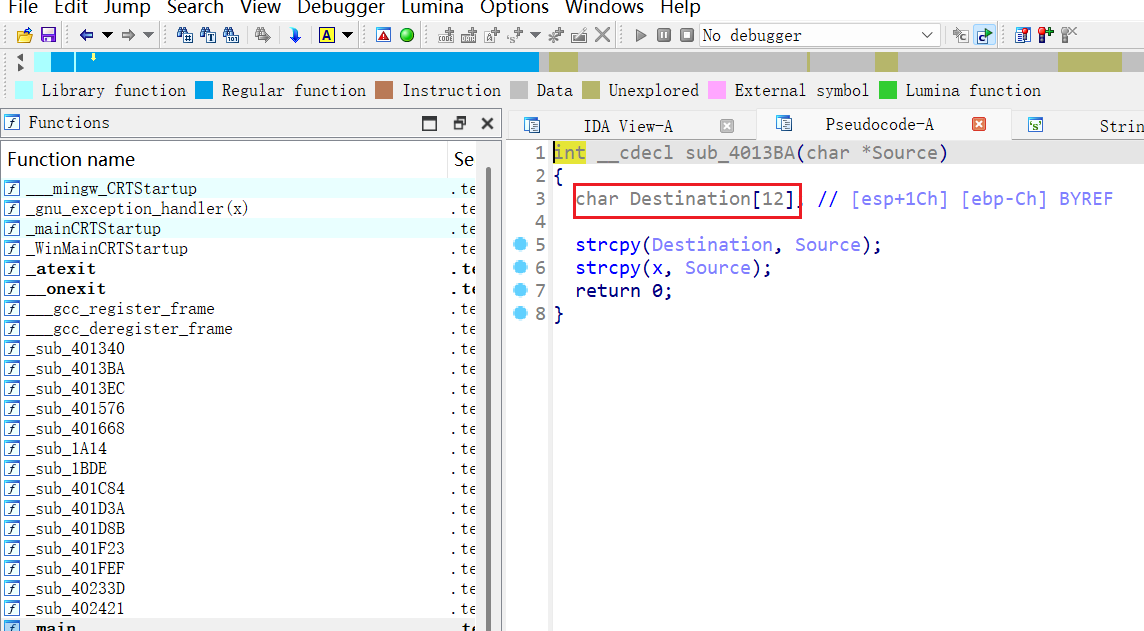
Destination[12]长度只有12,而第一部分长度位16,也就是说溢出了4,刚好把栈底填满(32位程序),返回地址传入了_X的地址
传入的地址为40233D,即为ret返回的地址
- 验证
1 | flag = 'flag{Re_1s_So0_funny!' |
BJDCTF
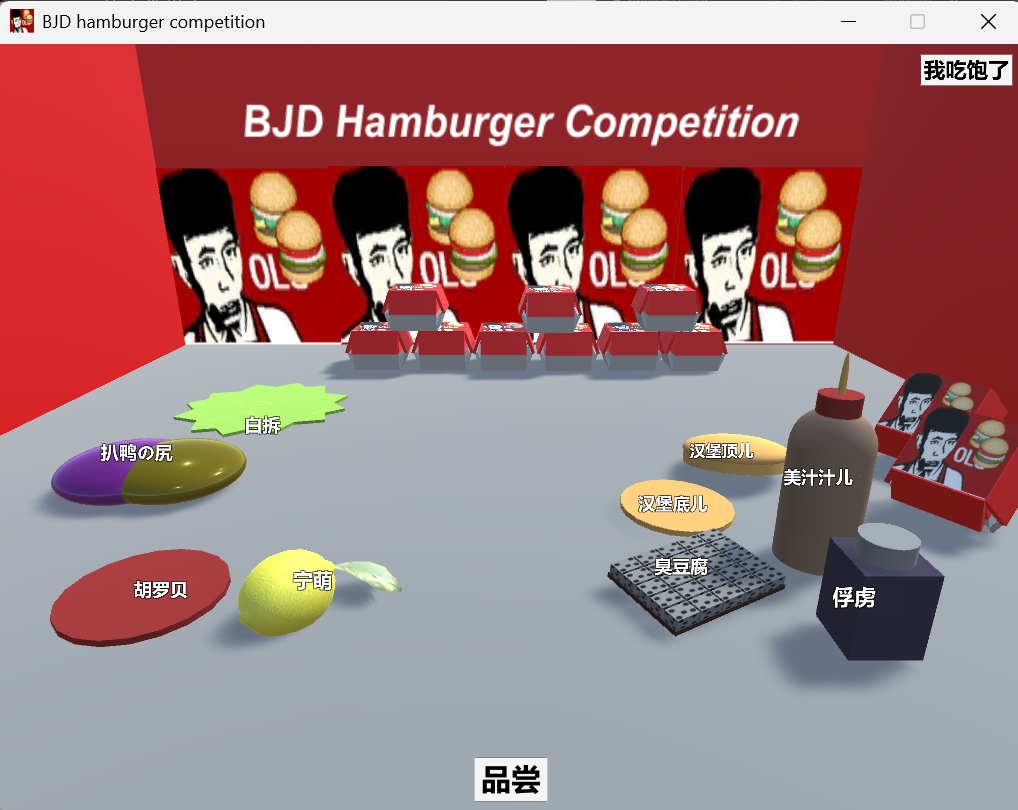
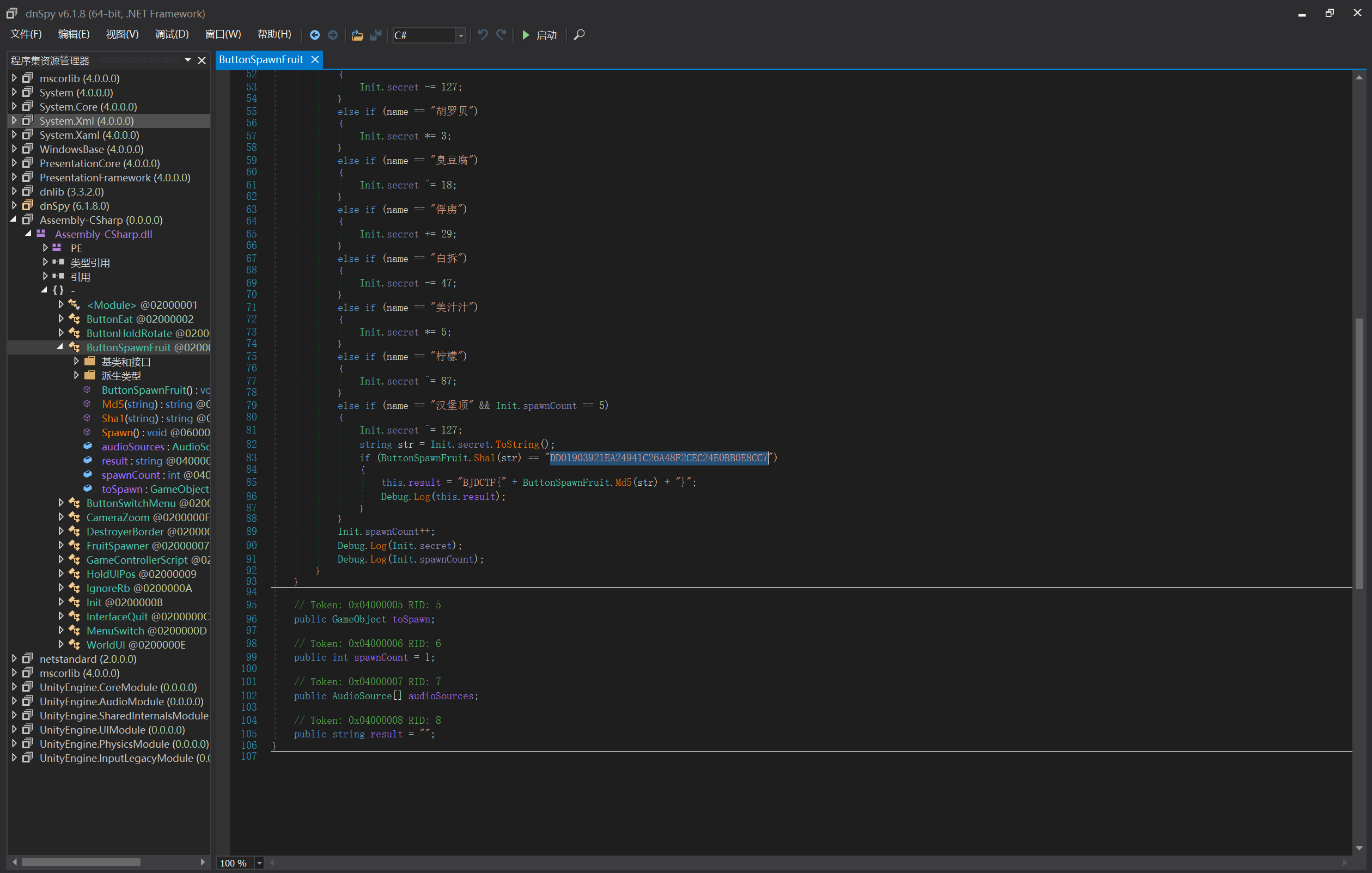
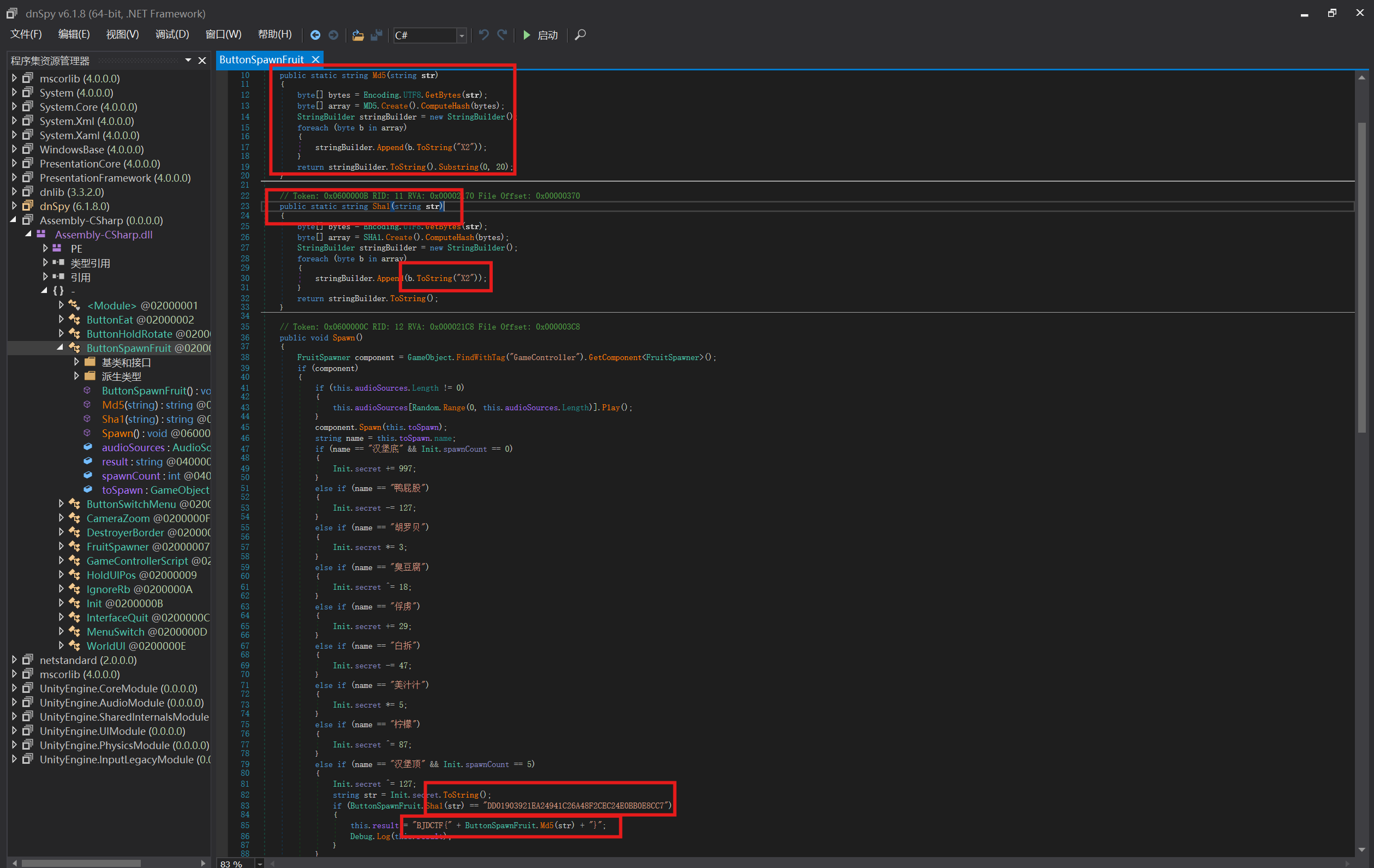
[BJDCTF2020]BJD-hamburger-competition
- 第一次做的Unity3D题目,抽象的老八秘制小汉堡游戏
1 | Unity3D是由Unity Technologies开发的一个让玩家轻松创建互动内容的多平台的综合型游戏开发工具, |
- 意思是
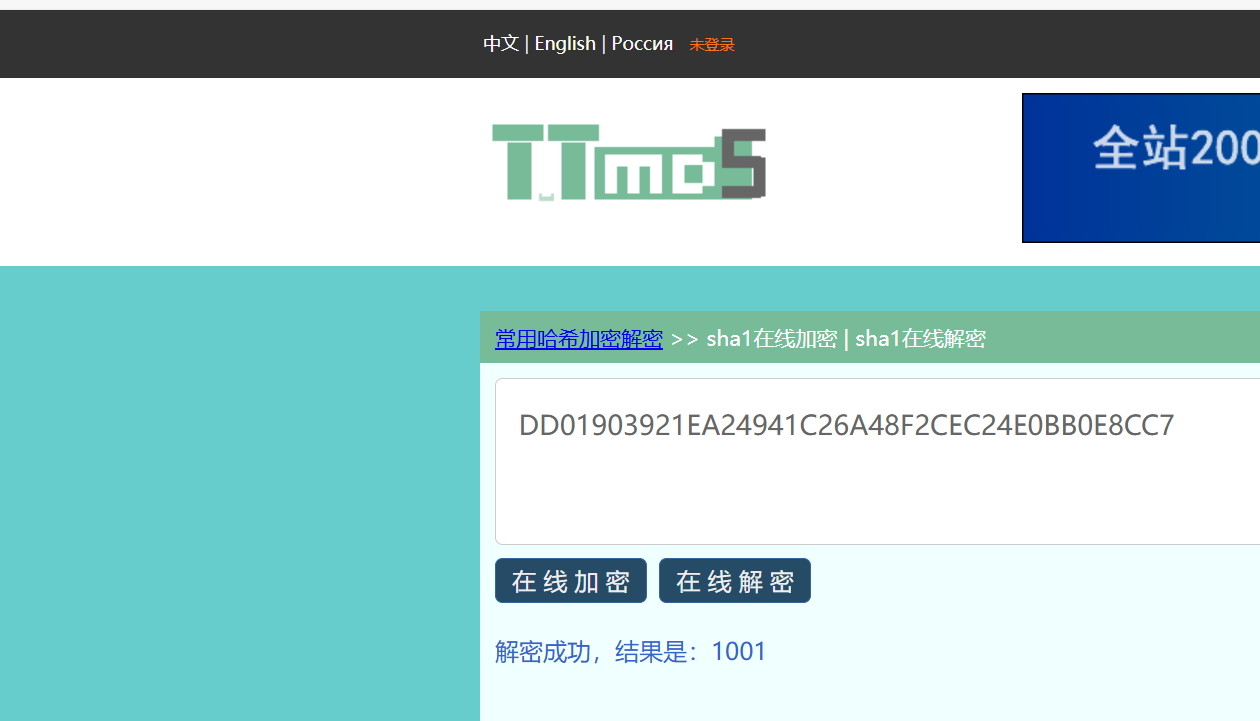
sha1对str加密结果为图中那一串,再用str的MD5的前20位作为flag
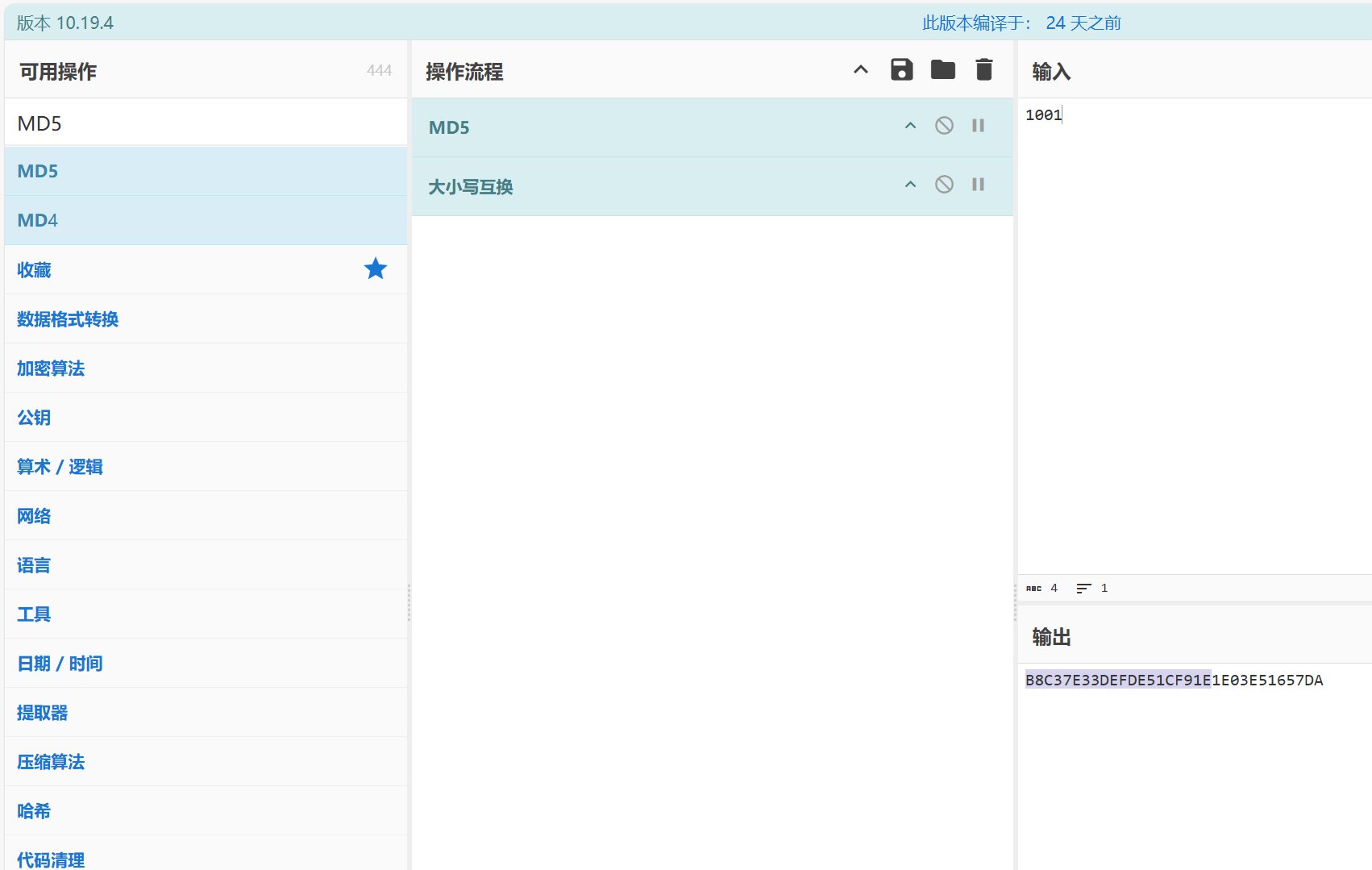
- 所以在线sha1解密,在MD5加密就行
1 | B8C37E33DEFDE51CF91E1E03E51657DA |
取前20个
1 | flag{B8C37E33DEFDE51CF91E} |
MRCTF
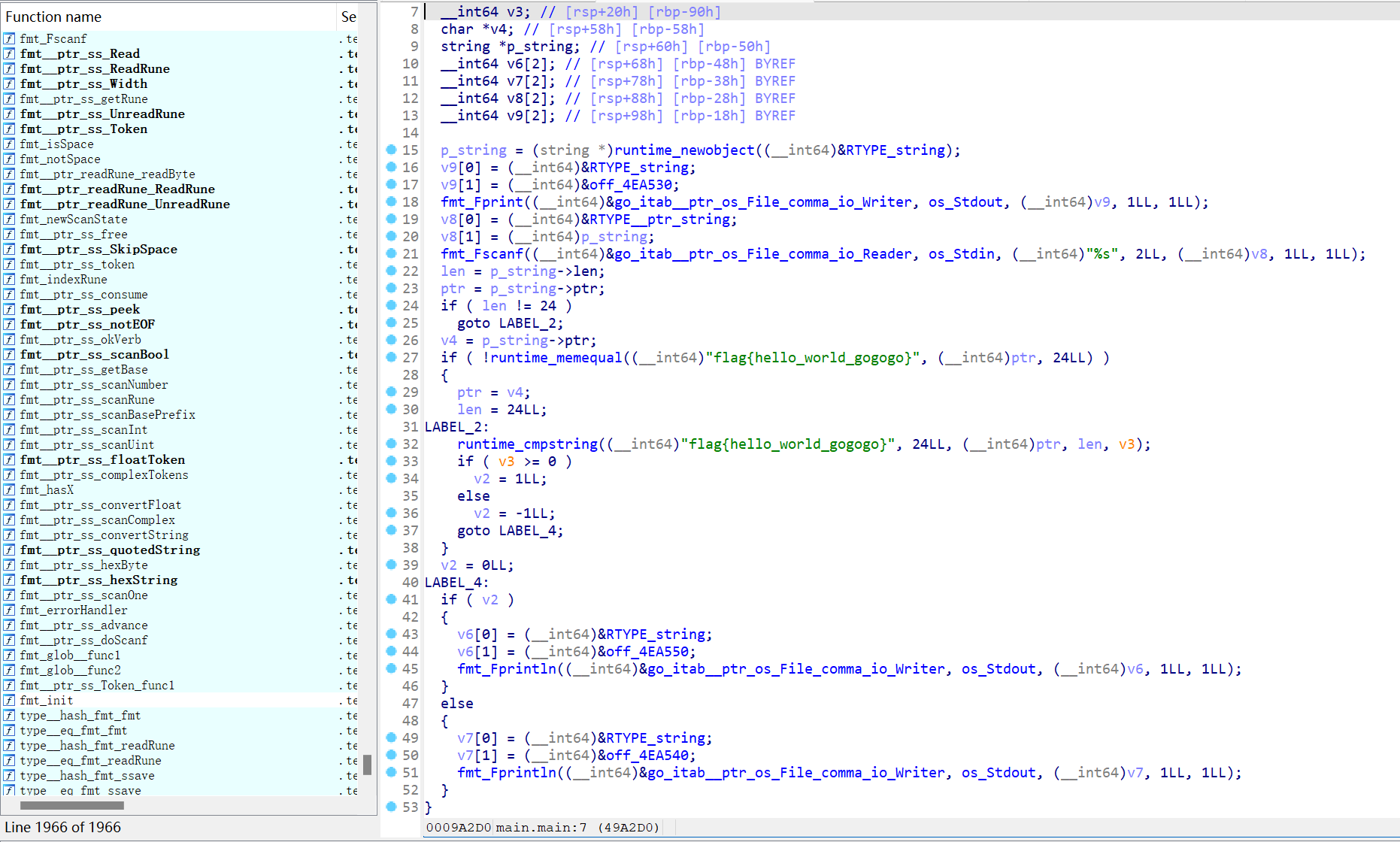
[MRCTF2020]hello_world_go
- 应该是个签到题,IDA打开就是flag
[MRCTF2020]PixelShooter
- unity游戏逆向还得是dnspy
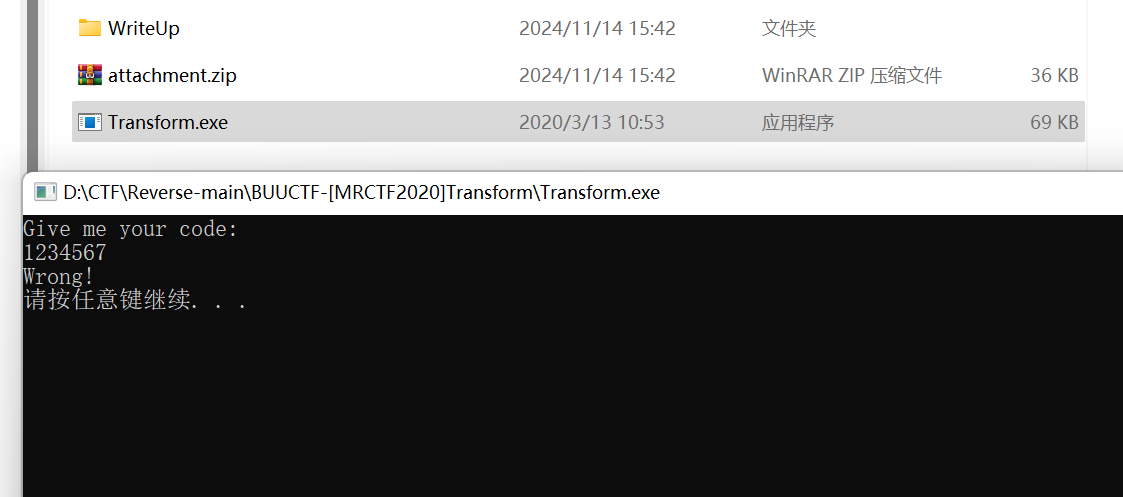
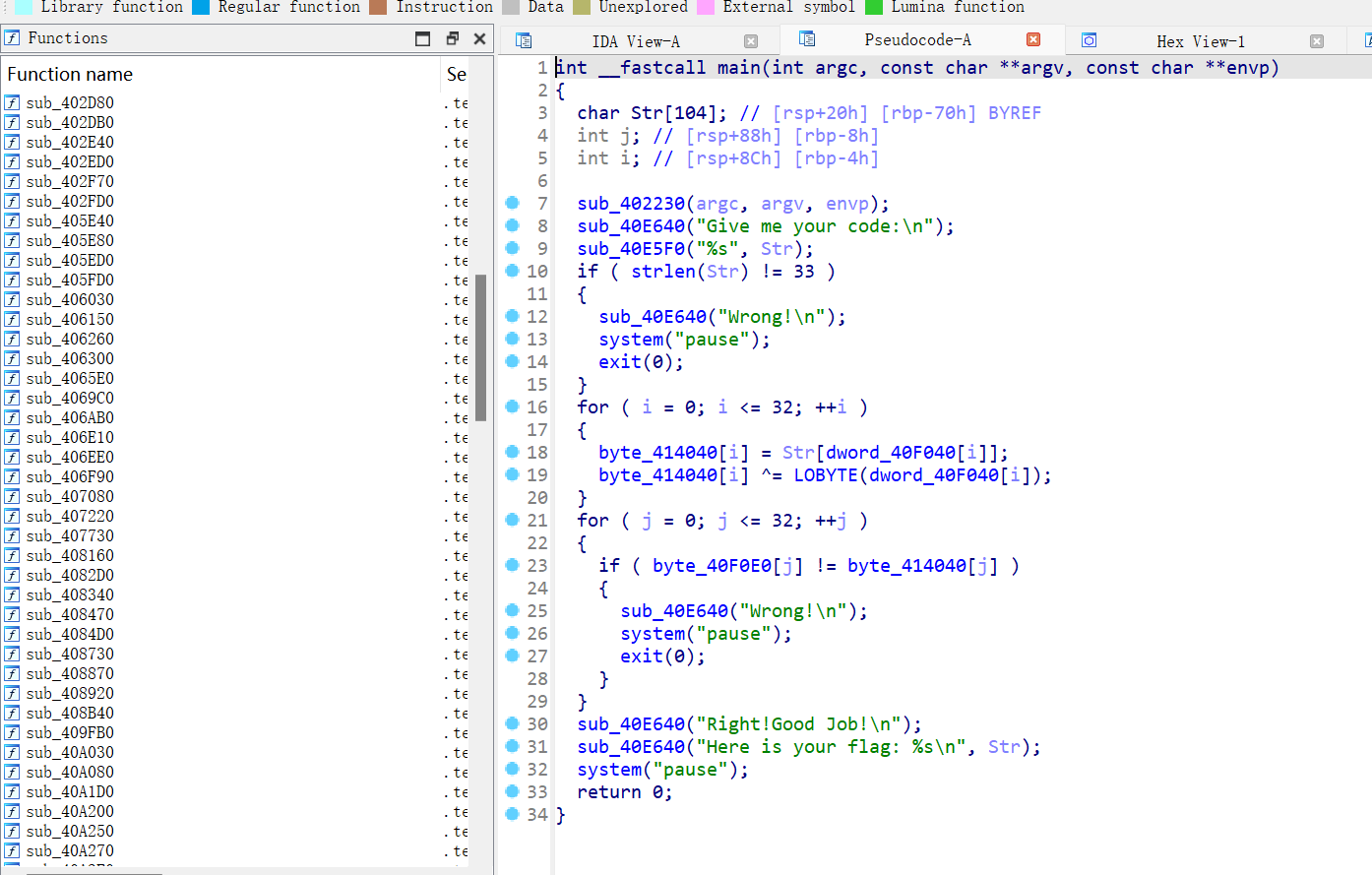
[MRCTF2020]Transform
- 64位,无壳
- 不懂,搜的,但对解题没影响,因为提取的数据(data)都小于2^8^=128
1 | 对于 LOBYTE(9),我们首先需要理解 LOBYTE 宏的作用:它提取一个 16 位数的低 8 位部分。 |
- 脚本
1 | data = [ |
GWCTF
HDCTF
WUSTCTF
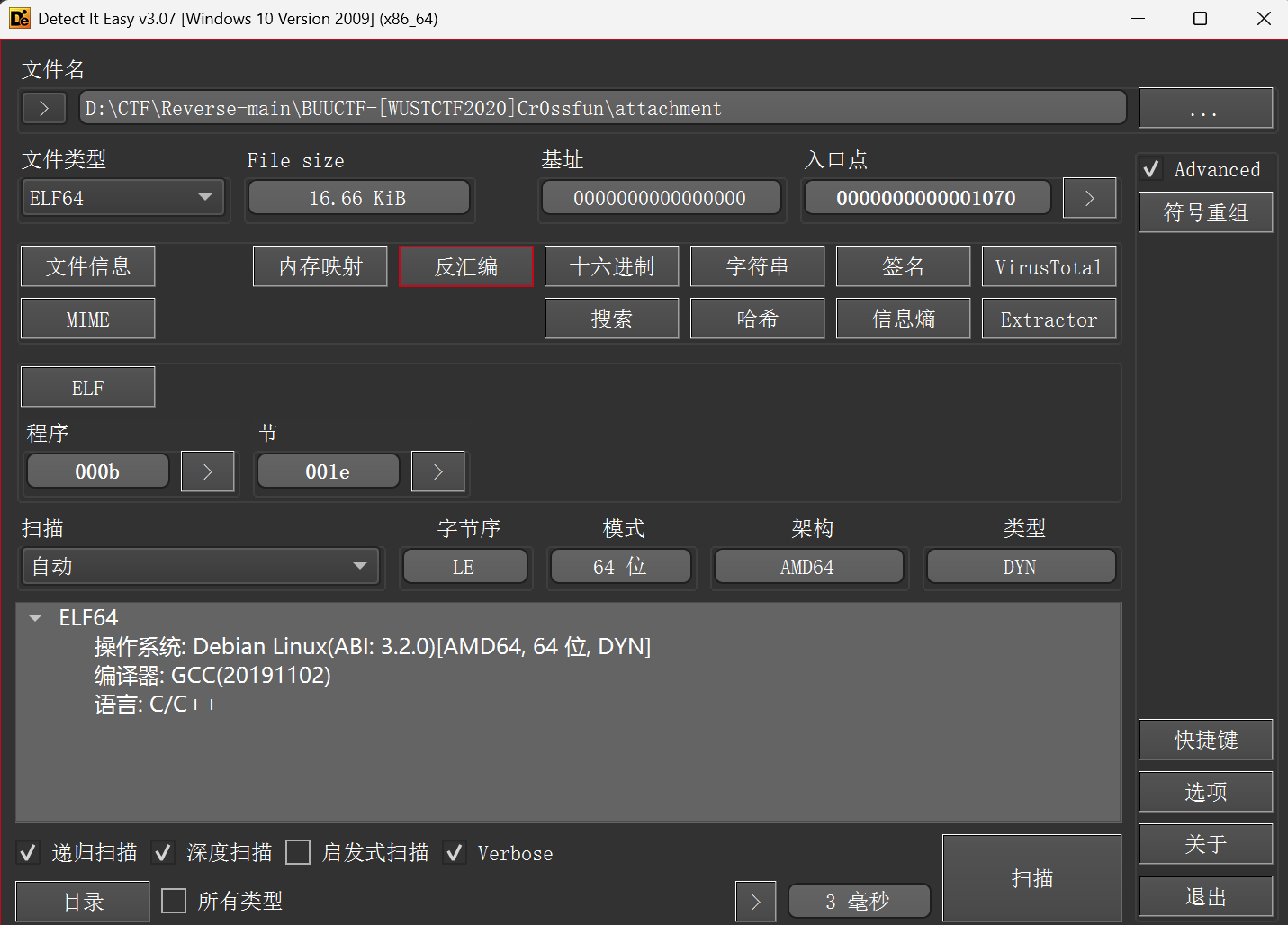
[WUSTCTF2020]Cr0ssfun
- 查壳,无
- 单纯的套娃拼接,直接让kimi帮我提取了
1 | _BOOL8 __fastcall iven_is_handsome(_BYTE *a1) |
- 最后用flag{}包裹
1 | # cctf2000{cpp_@nd_r3verse_@re_fun} |
[WUSTCTF2020]level2
- UPX加壳了
upx -d去壳

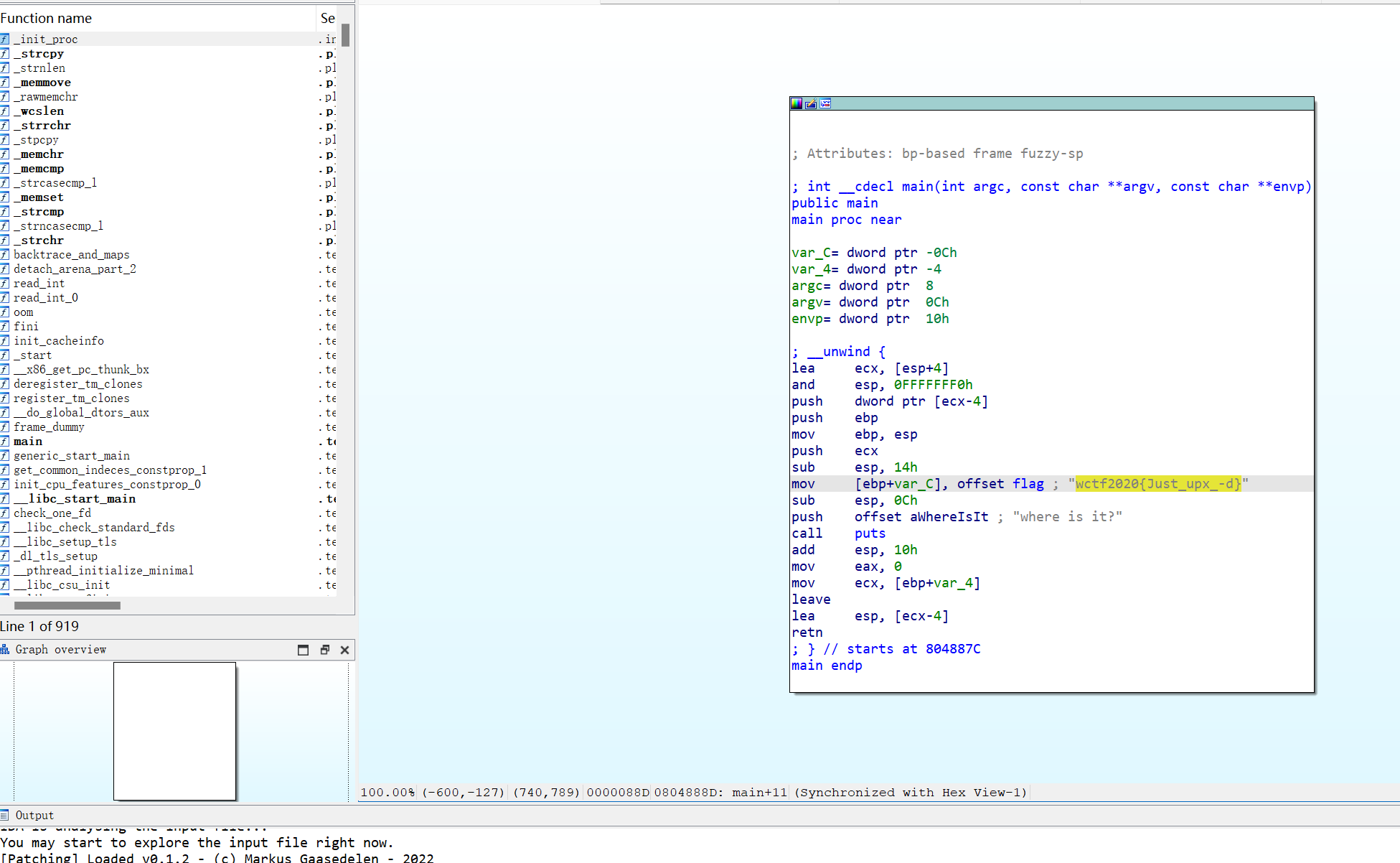
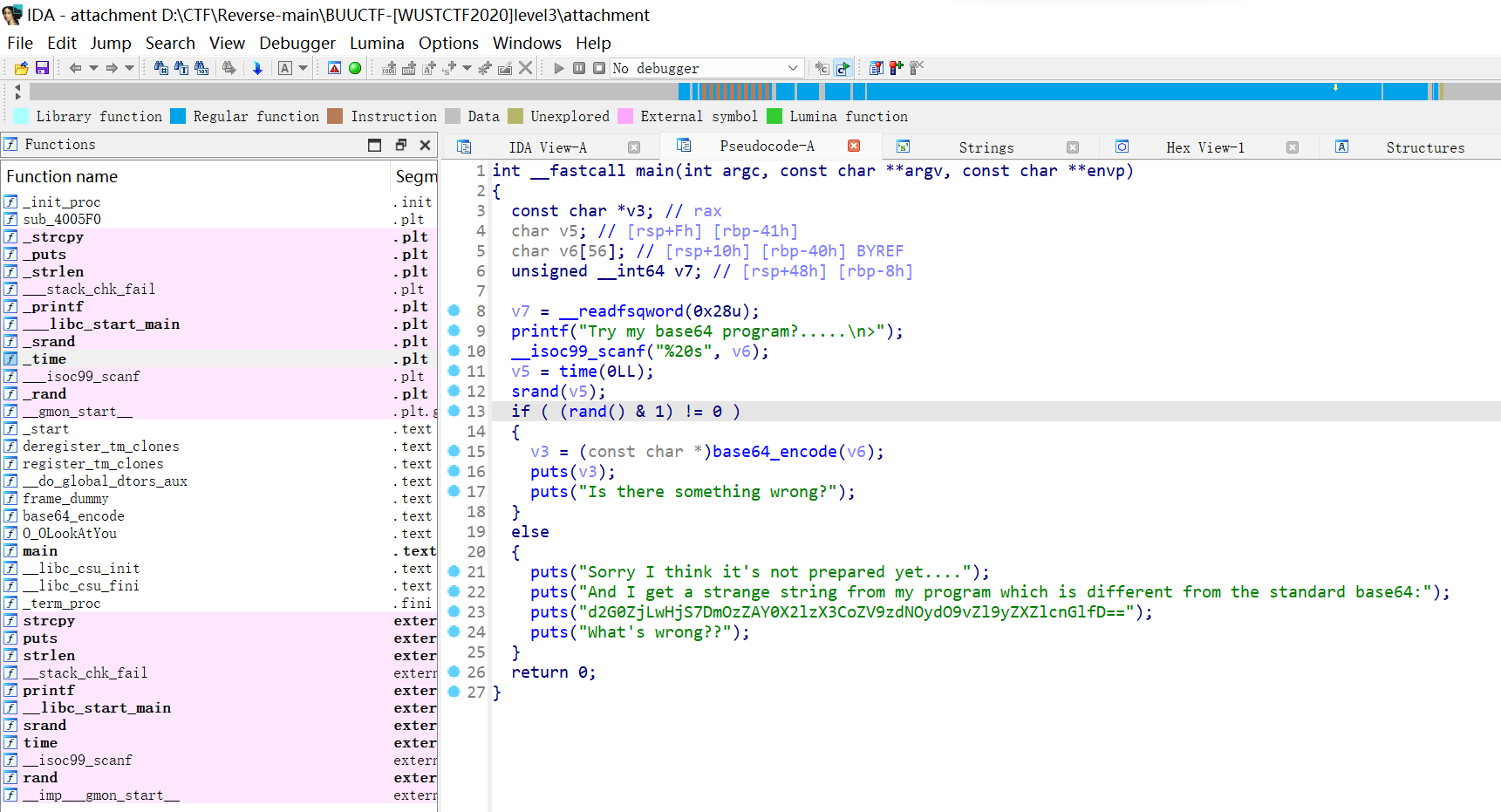
[WUSTCTF2020]level3
- 明示是Base64加密,shift+F12找到密文,用赛博厨子解密了一下,不对
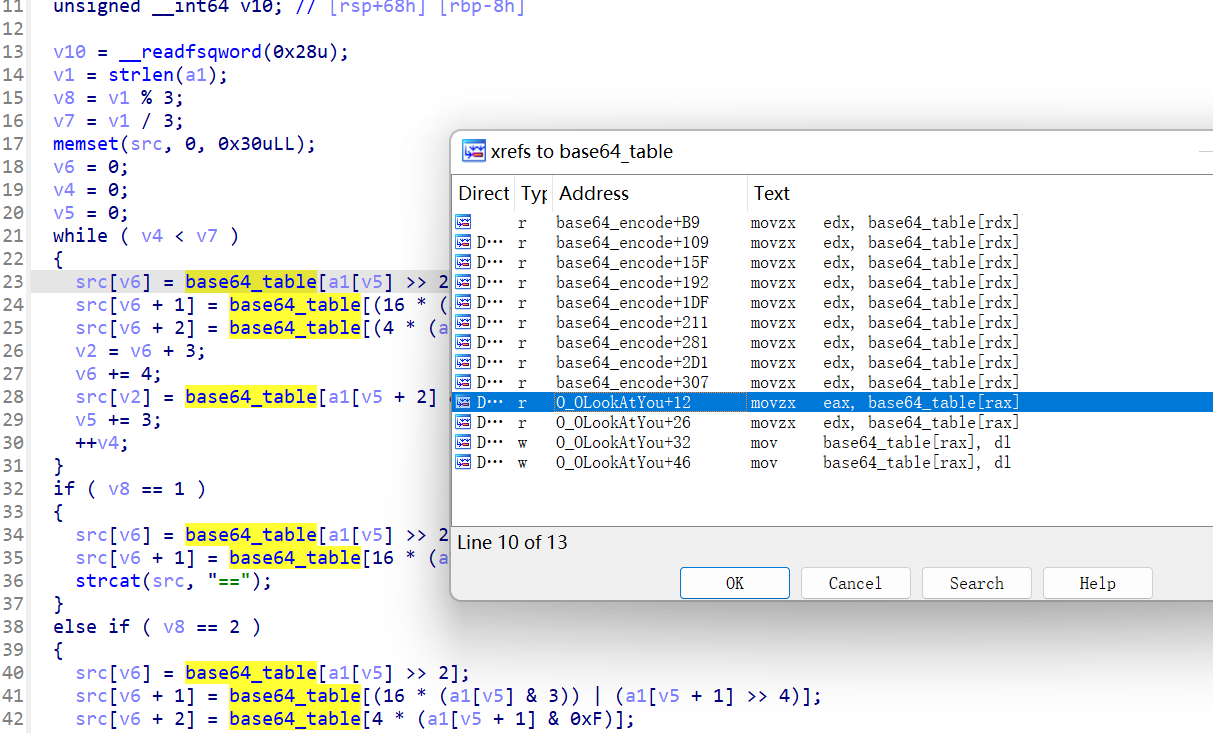
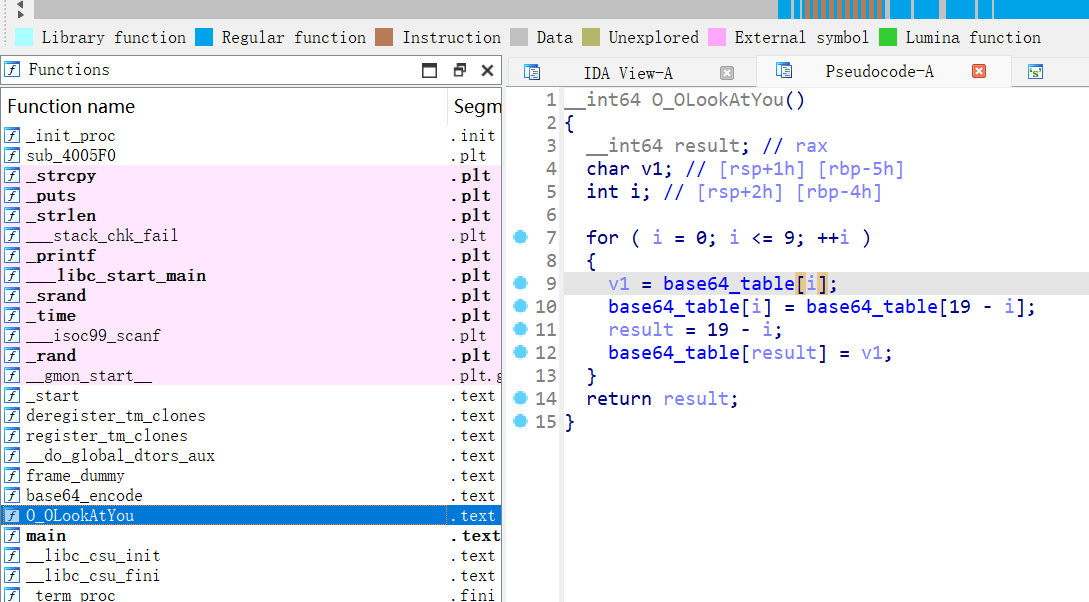
- 查看Base64表,按 X 查看表的引用,果然不对劲,发现有对表的操作
1 | base64_table = [ |
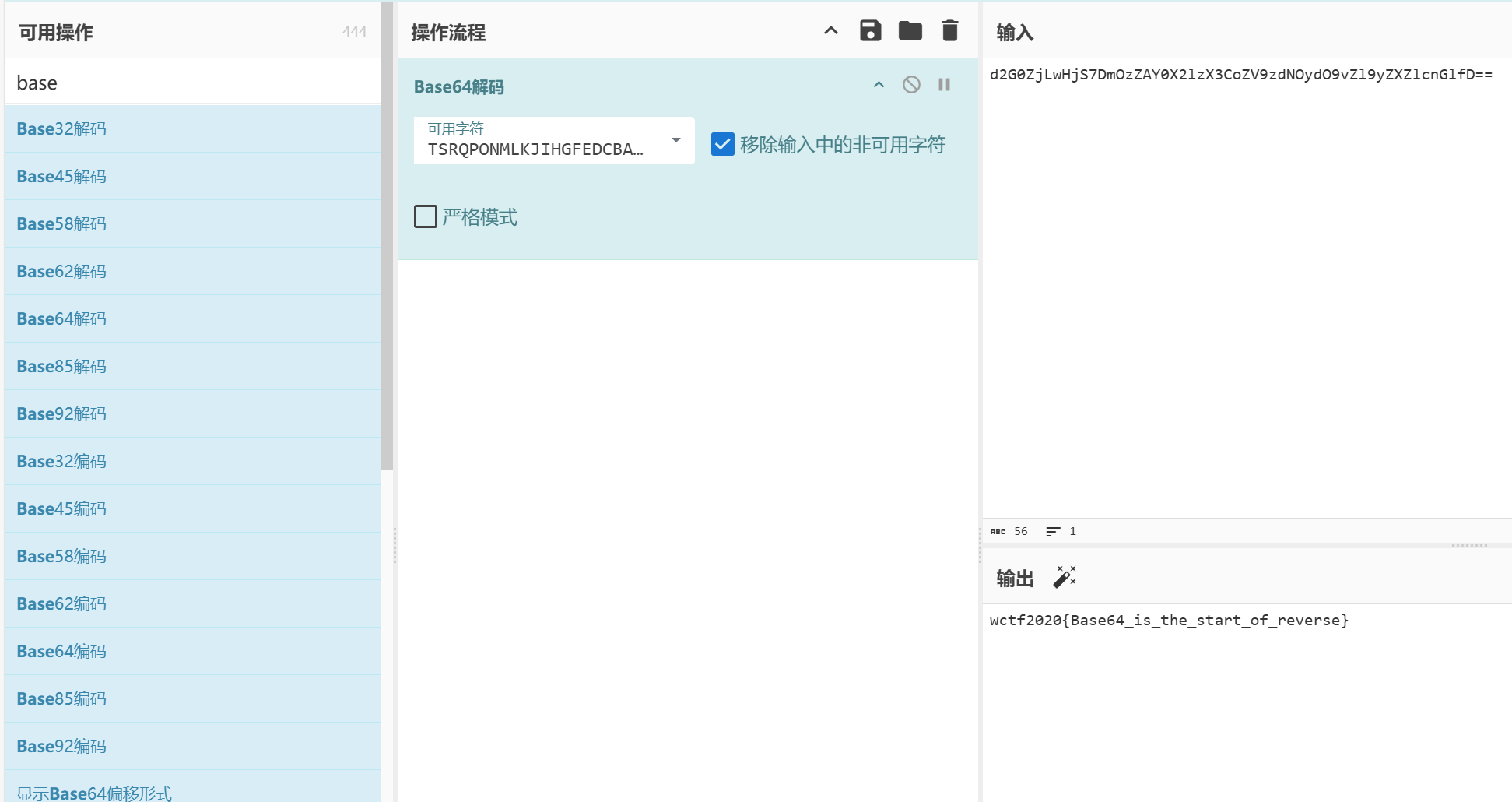
- 换表,赛博厨子解一下
1 | wctf2020{Base64_is_the_start_of_reverse} |
- 之前看到的一个wp里的脚本,挺有意思的,直接本地换表(映射)解密,在这贴一下
1 | import base64 #导入base64模块用于解密 |
exp:
1 | import base64 |
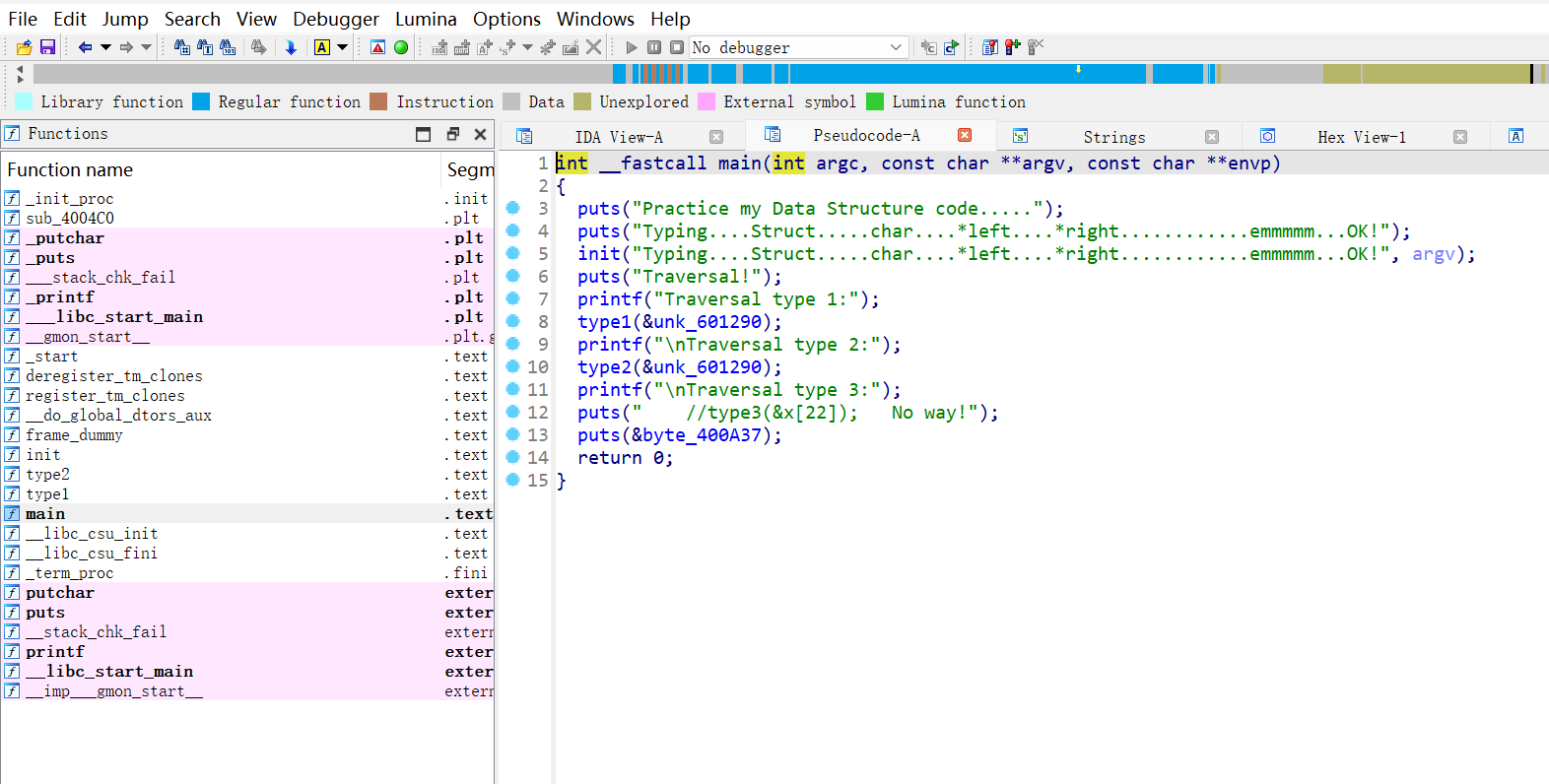
[WUSTCTF2020]level4
- 64位,无壳
一眼没看出来,仔细看了才知道,
Date Structure考了个数据结构二叉树中序遍历
1 | __int64 __fastcall type1(char *a1) |
- 二叉树后序遍历
1 | int __fastcall type2(char *a1) |
- 程序运行的结果
1 | Traversal type 1:2f0t02T{hcsiI_SwA__r7Ee} |
- 已知后序中序输出前序
1 | def build_tree(post, mid): |
Other
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Elliot-Lin!