FlareOnCTF
FlareOnCTF 练习
[FlareOn4] IgniteMe
无壳, ida 打开
在
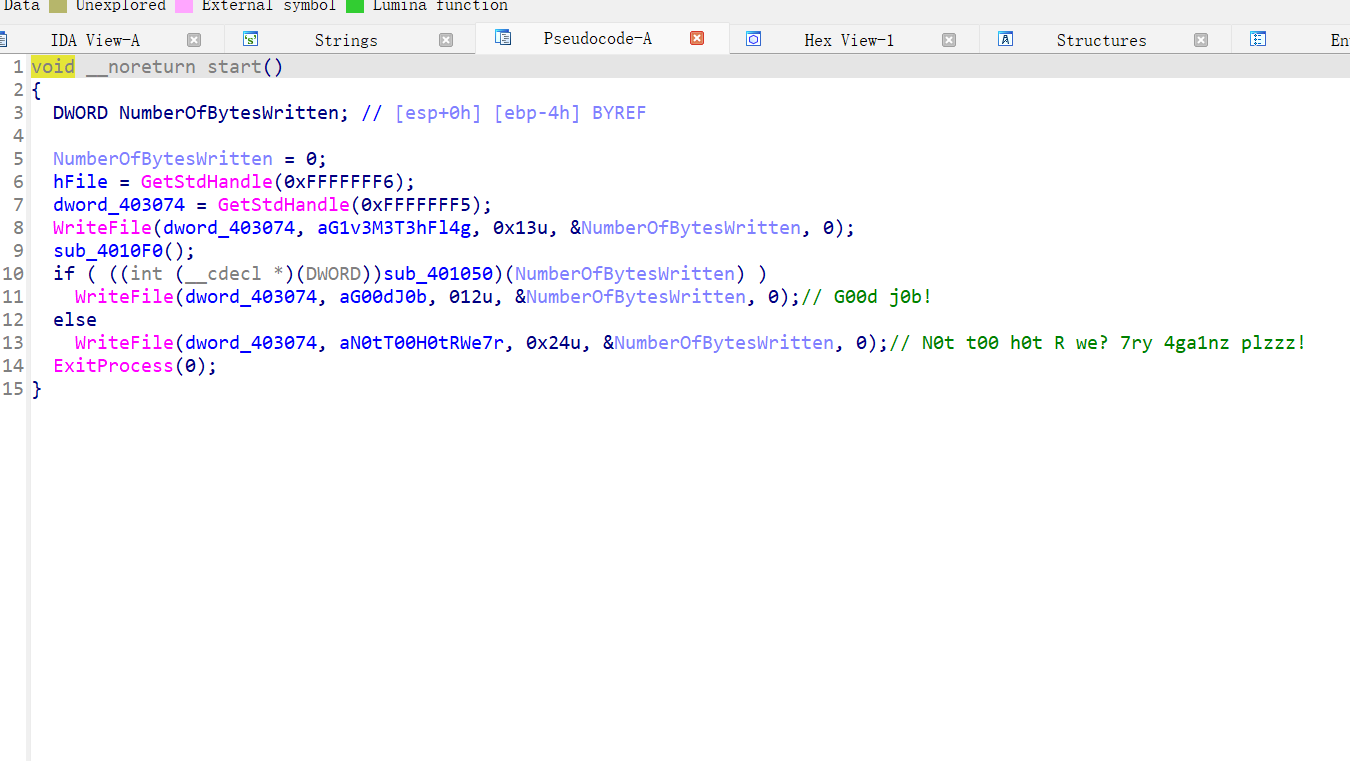
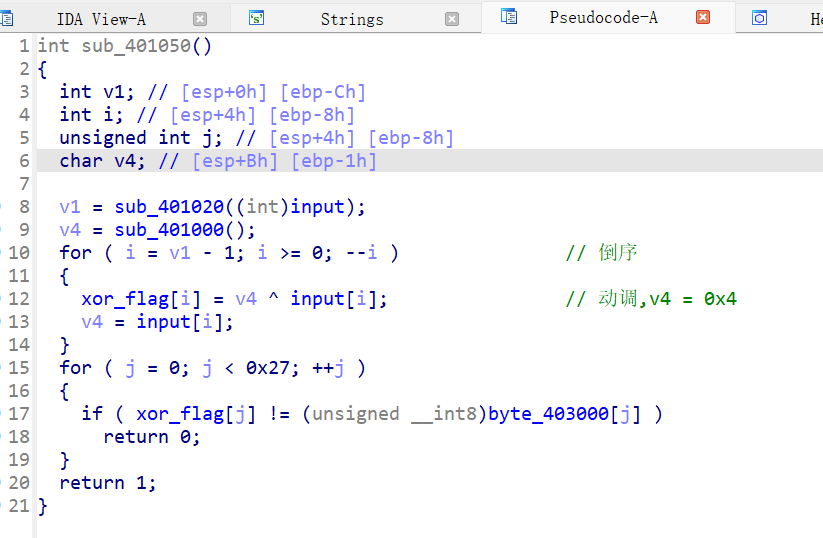
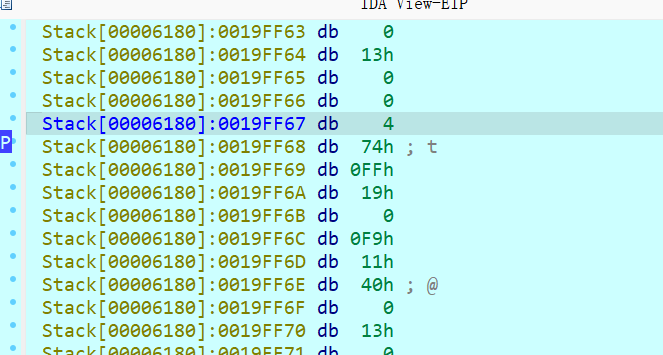
xor_flag[i] = v4 ^ input[i]处下断点,动态调试后就可以看到 v4 的值了,(把鼠标放 v4 上就可以显示值),不好截图,双击 v4 也可以看到值为 4最后, 从
最后一个开始异或前一个的运算易错的是,
v4 = a[i] ^ v4, 之前写成v4 = a[i]卡了好久
1 | a = [ |
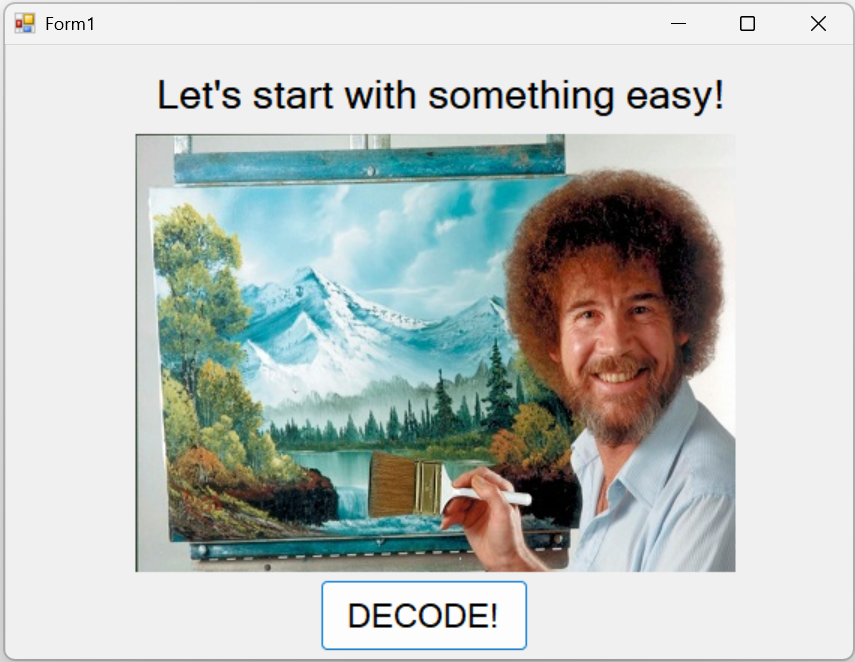
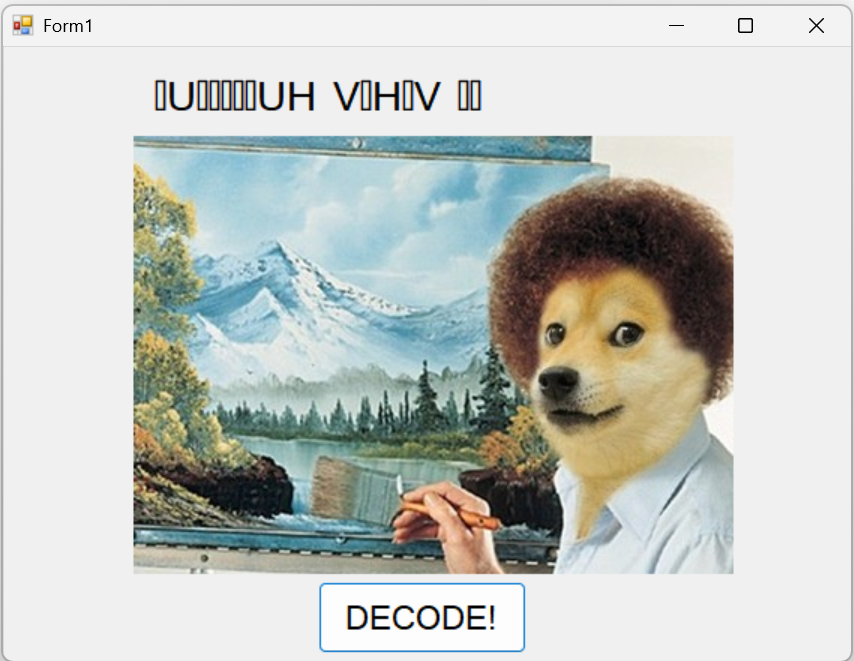
[FlareOn1] Bob-Doge
- 一个下载器,下载后运行是这个东西
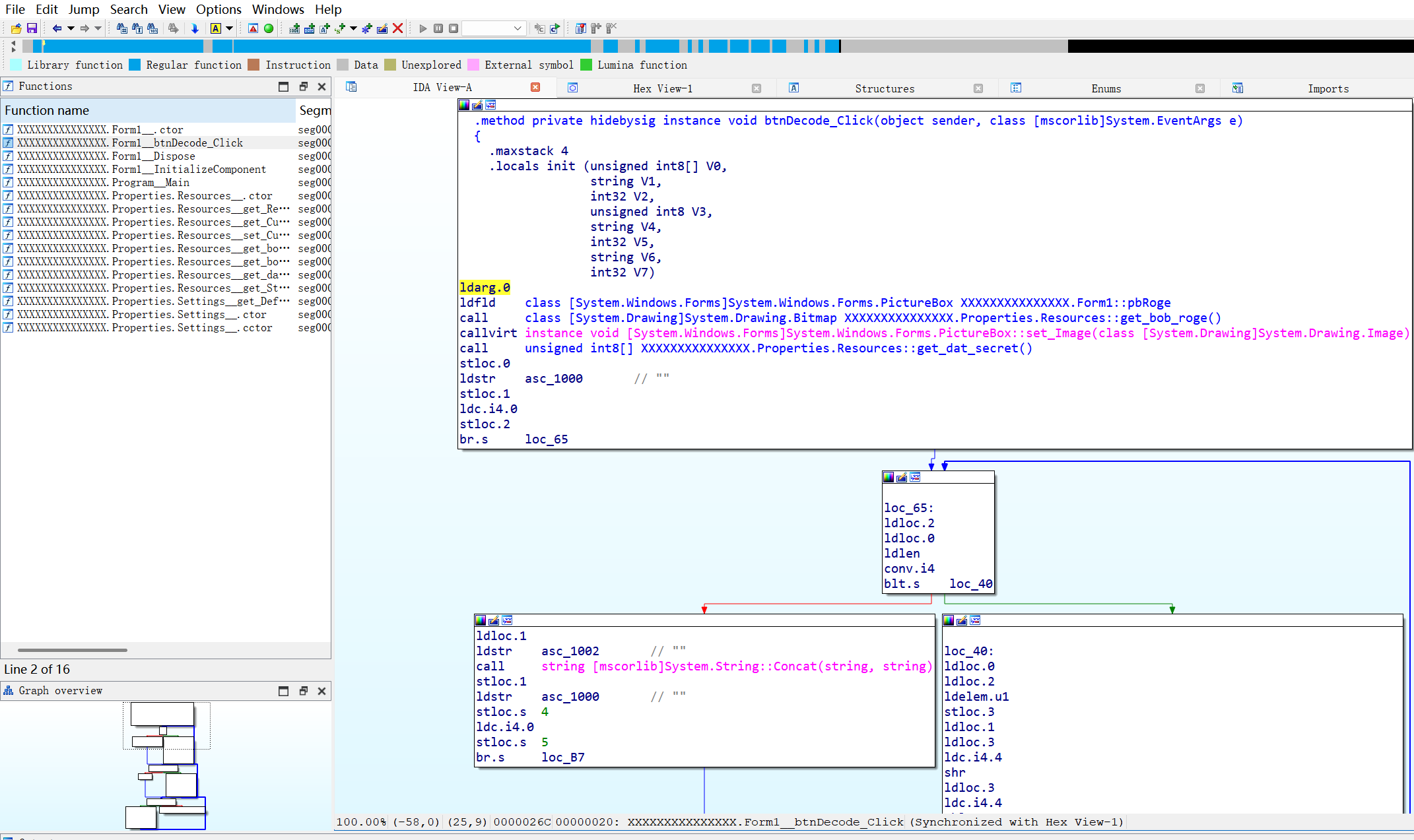
IDA 反编译, 看不懂没见过的形式
换一个工具, despy 打开, 看上舒服多了
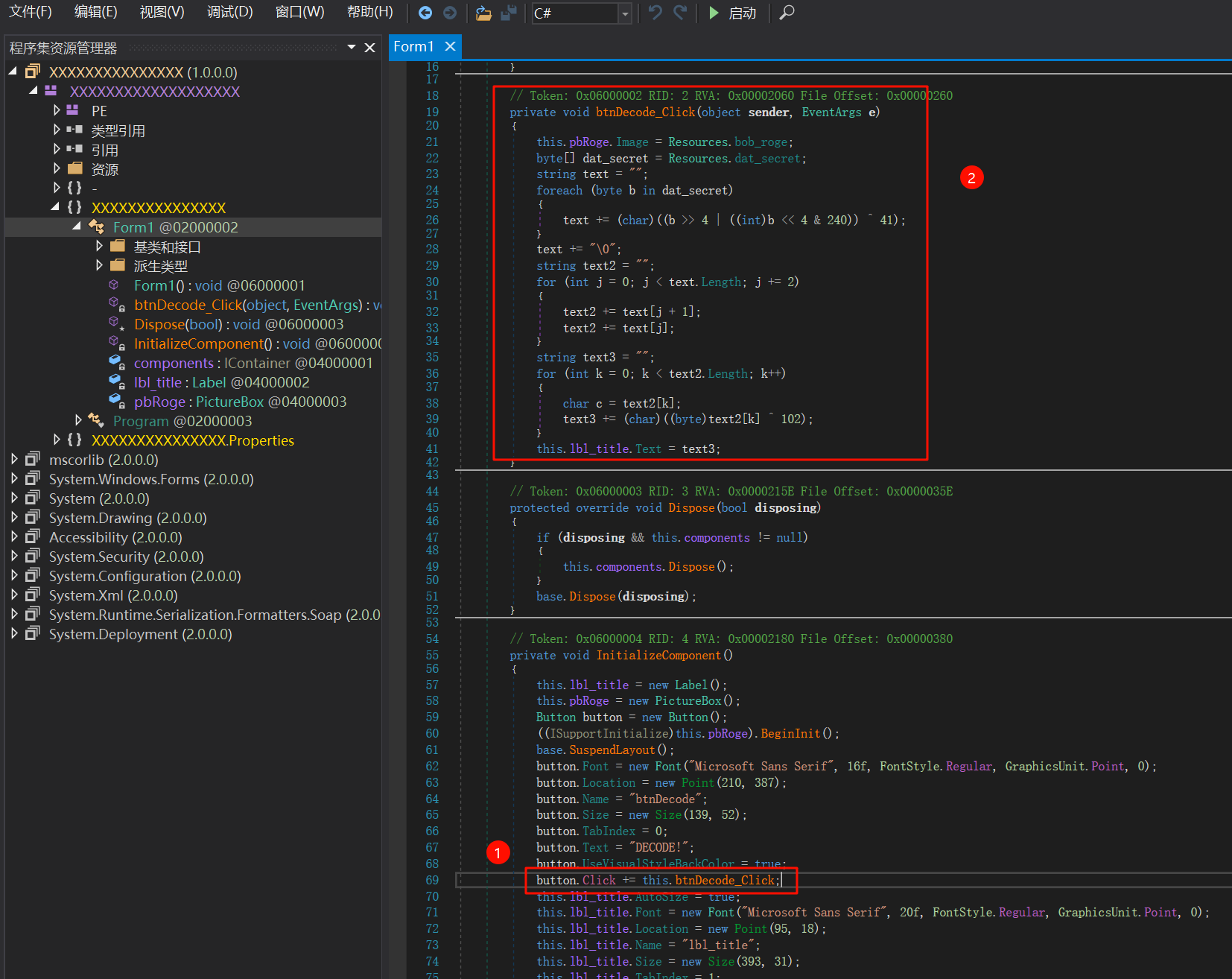
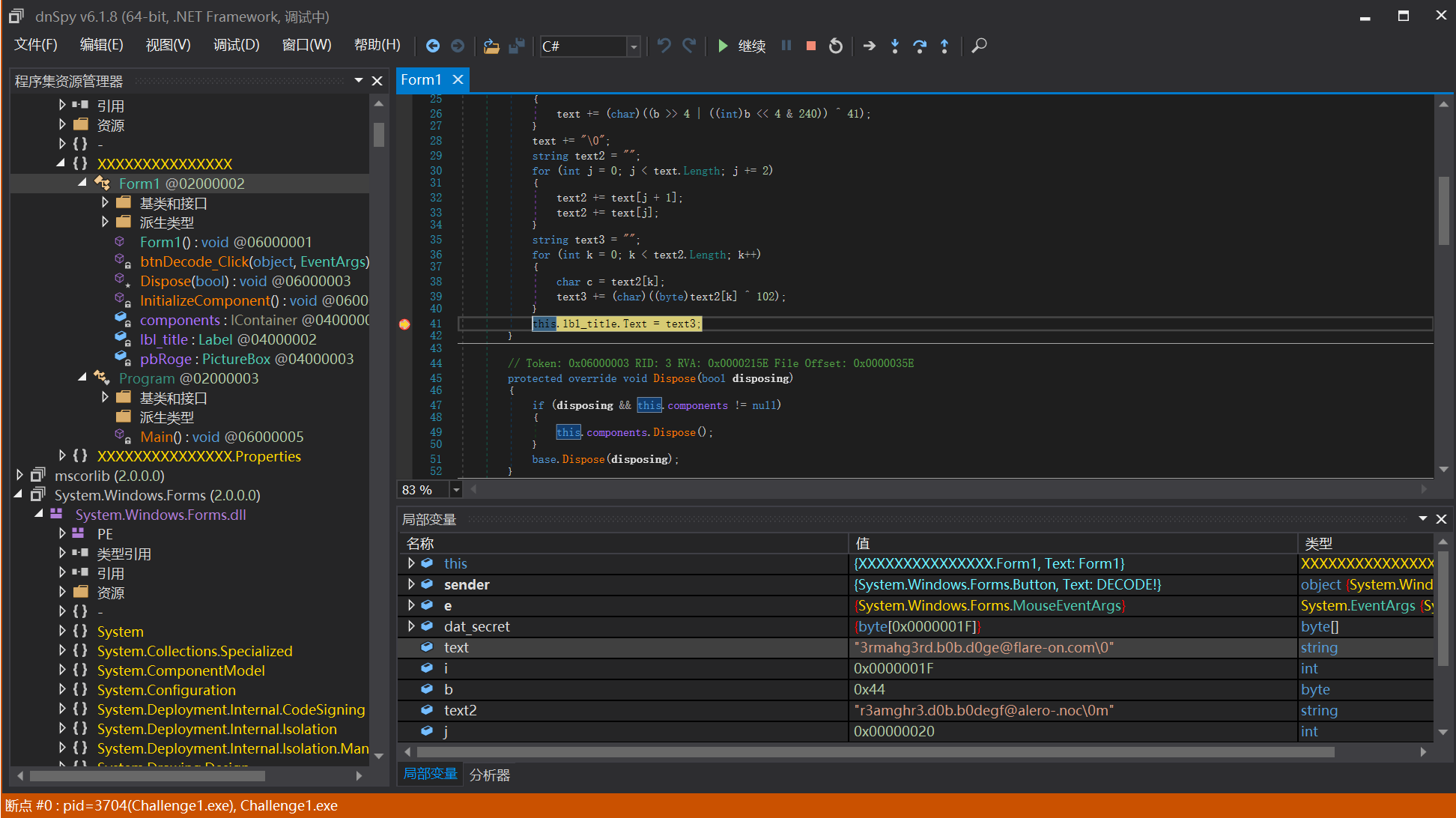
主要在这,
DECODE按钮事件,最终解码后的字符串text3显示在lbl_title标签中。
- 下断点,动态调试,直接看内容
[FlareOn3] Challenge1
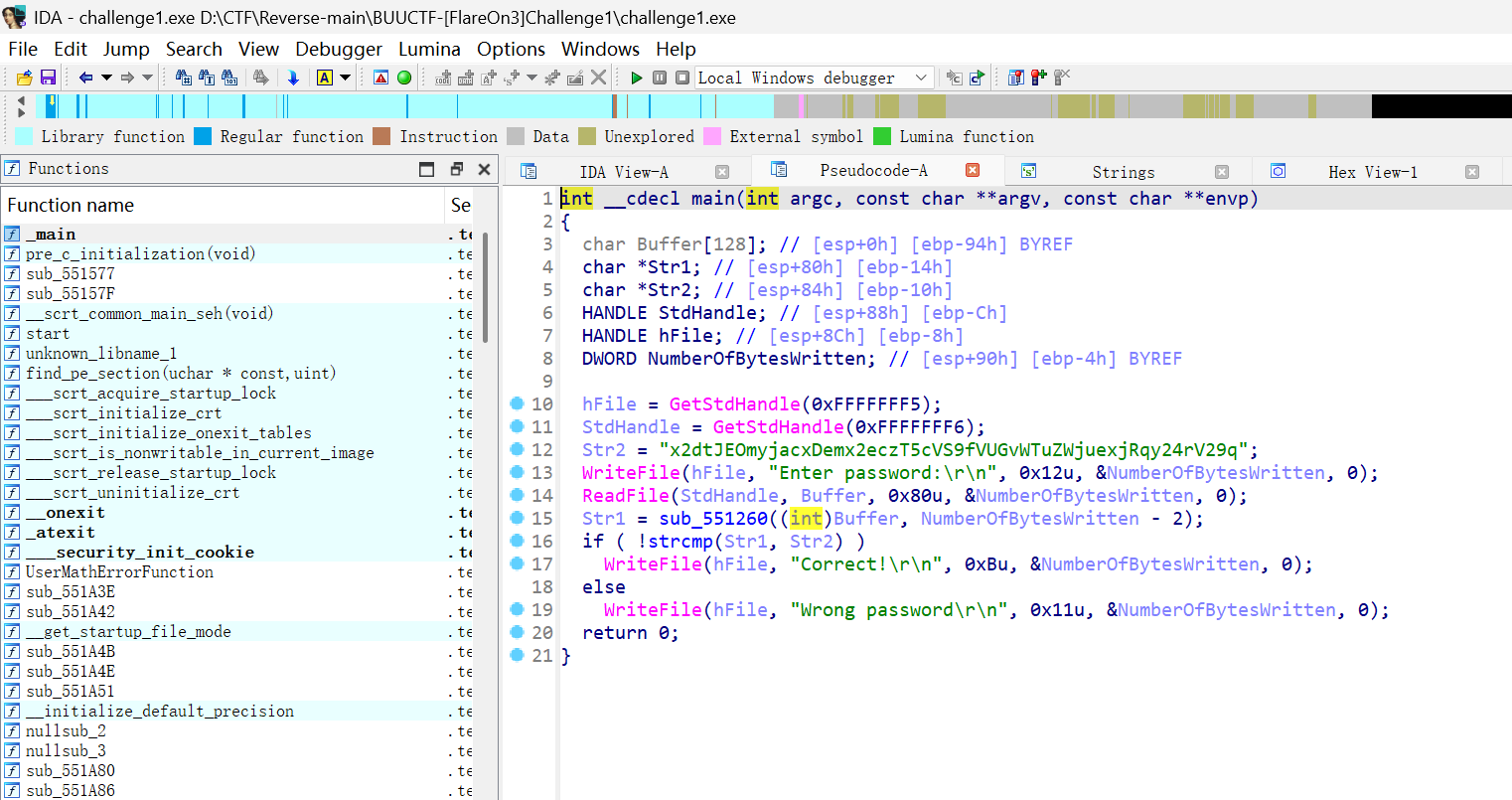
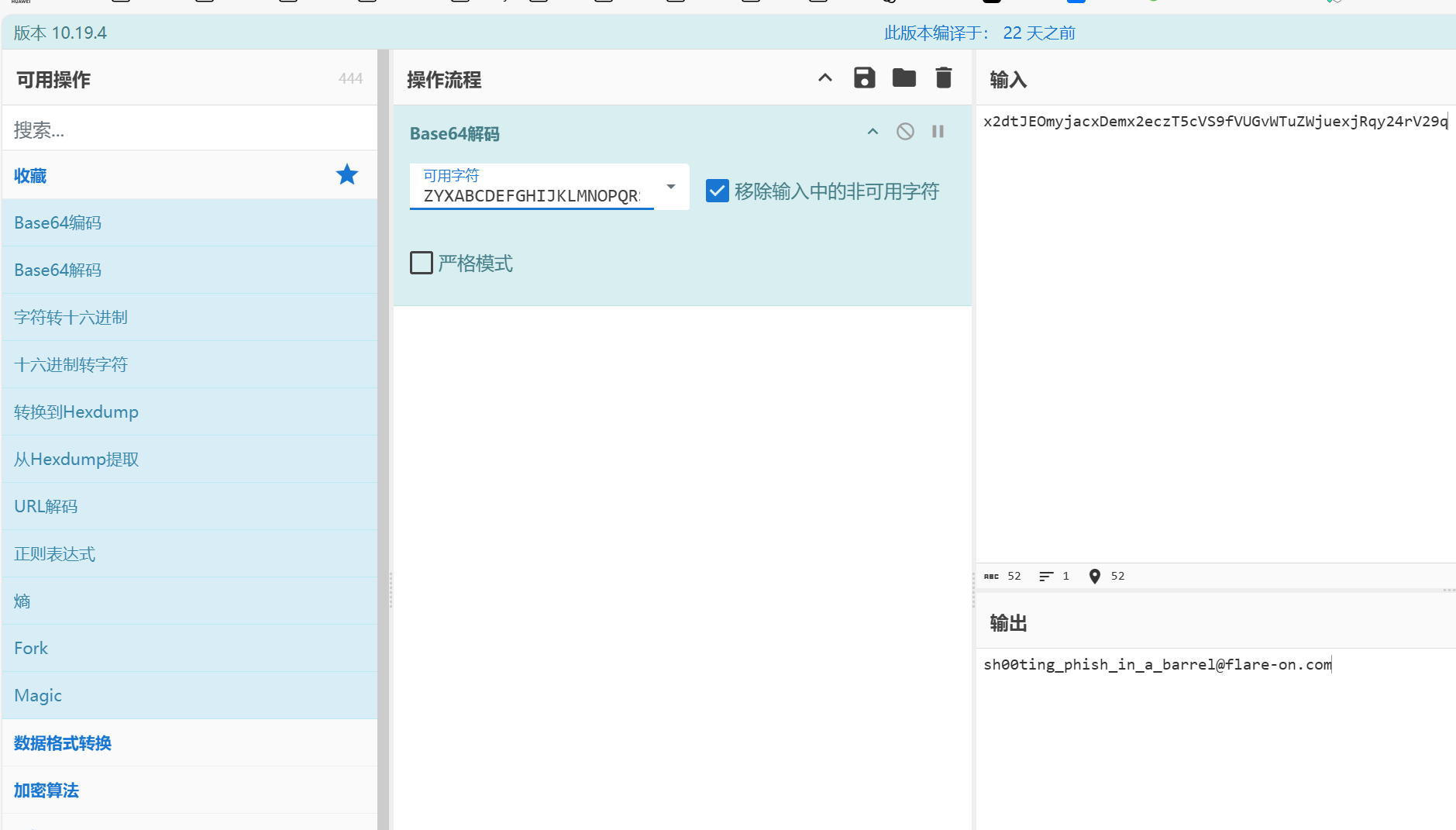
- base64 加密
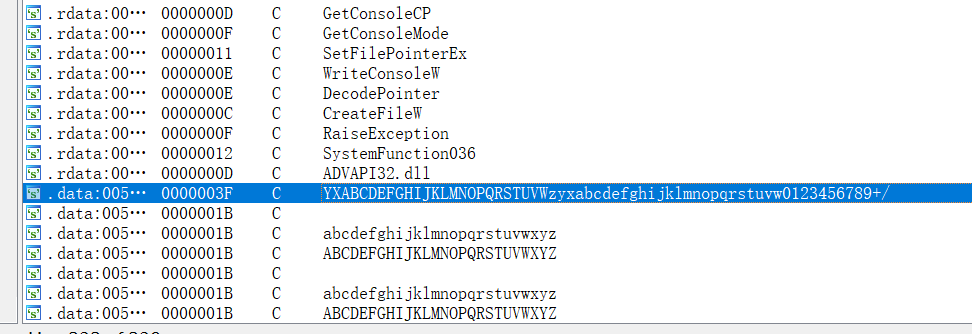
shift+f12查看字符串,发现换表了
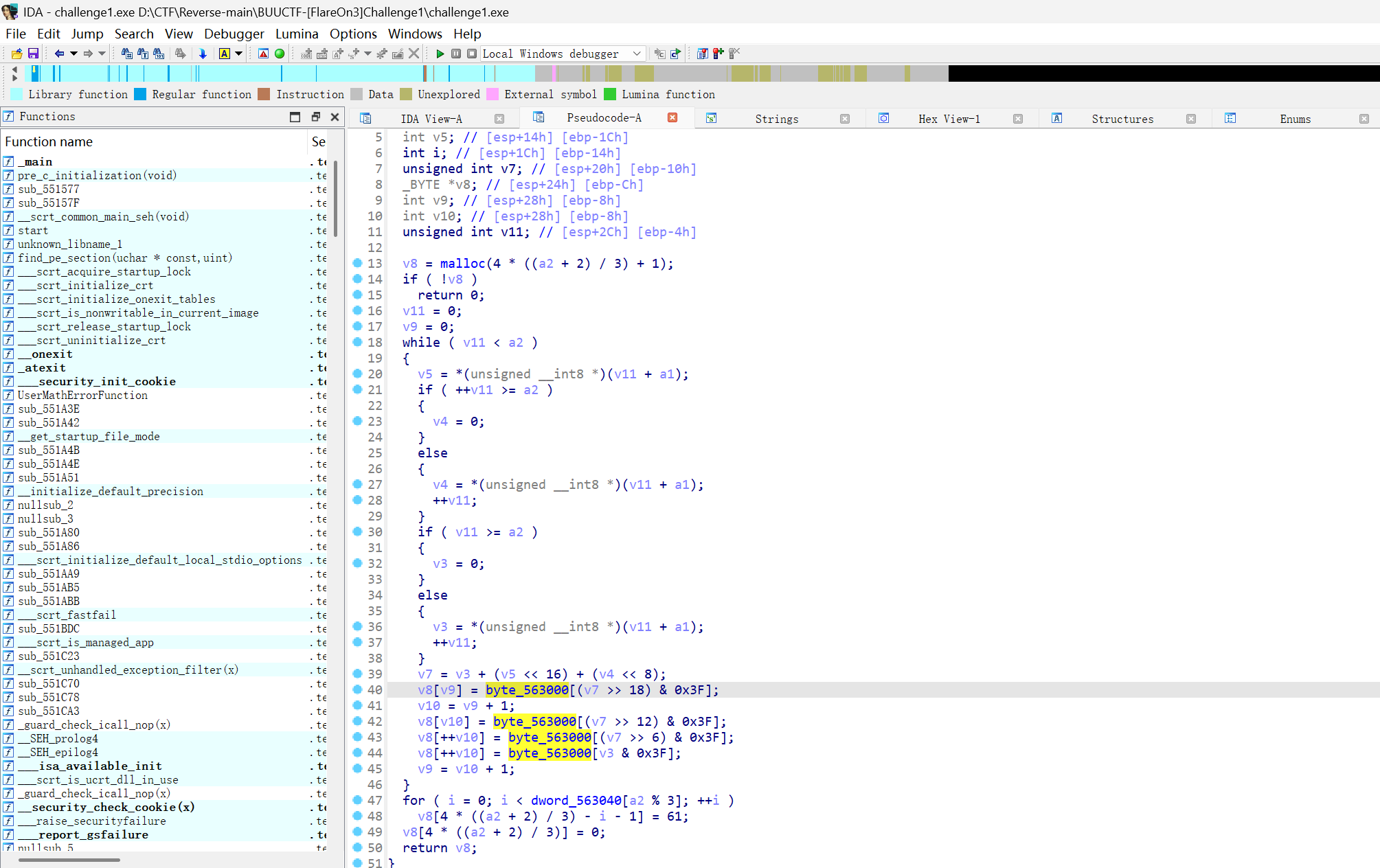
- 赛博厨子梭哈一下,根据后面小写的形式可知,换的表前面少了个
Z
1 | flag{sh00ting_phish_in_a_barrel@flare-on.com} |
[FlareOn6] Overlong
- 根据题目提示,这句话冒号
:后面应该还有内容
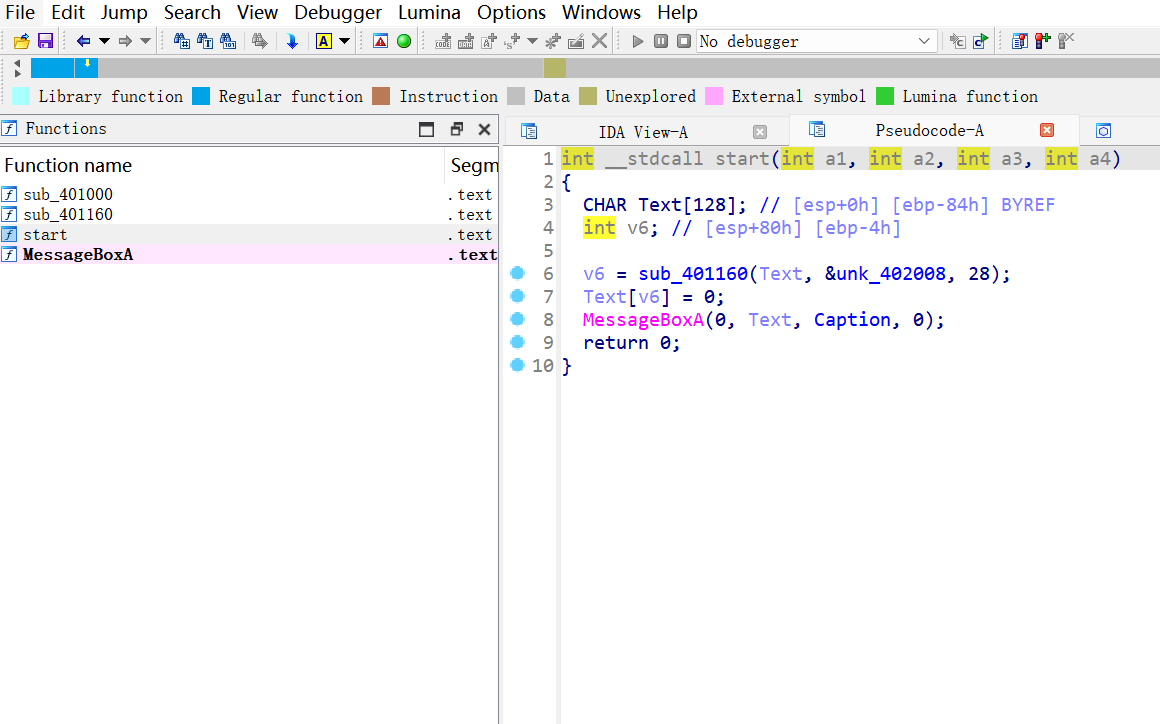
- 题目内容很少,都看一下
1 | int __stdcall start(int a1, int a2, int a3, int a4) |
- 这里进行加密
1 | int __cdecl sub_401000(unsigned __int8 *a1, char *a2) |
- 在
&unk_FB2008按shift+e提取数据,按加密写 python 脚本解密
1 | a2 = [0xe0, 0x81, 0x89, 0xc0, 0xa0, 0xc1, 0xae, 0xe0, 0x81, 0xa5, |
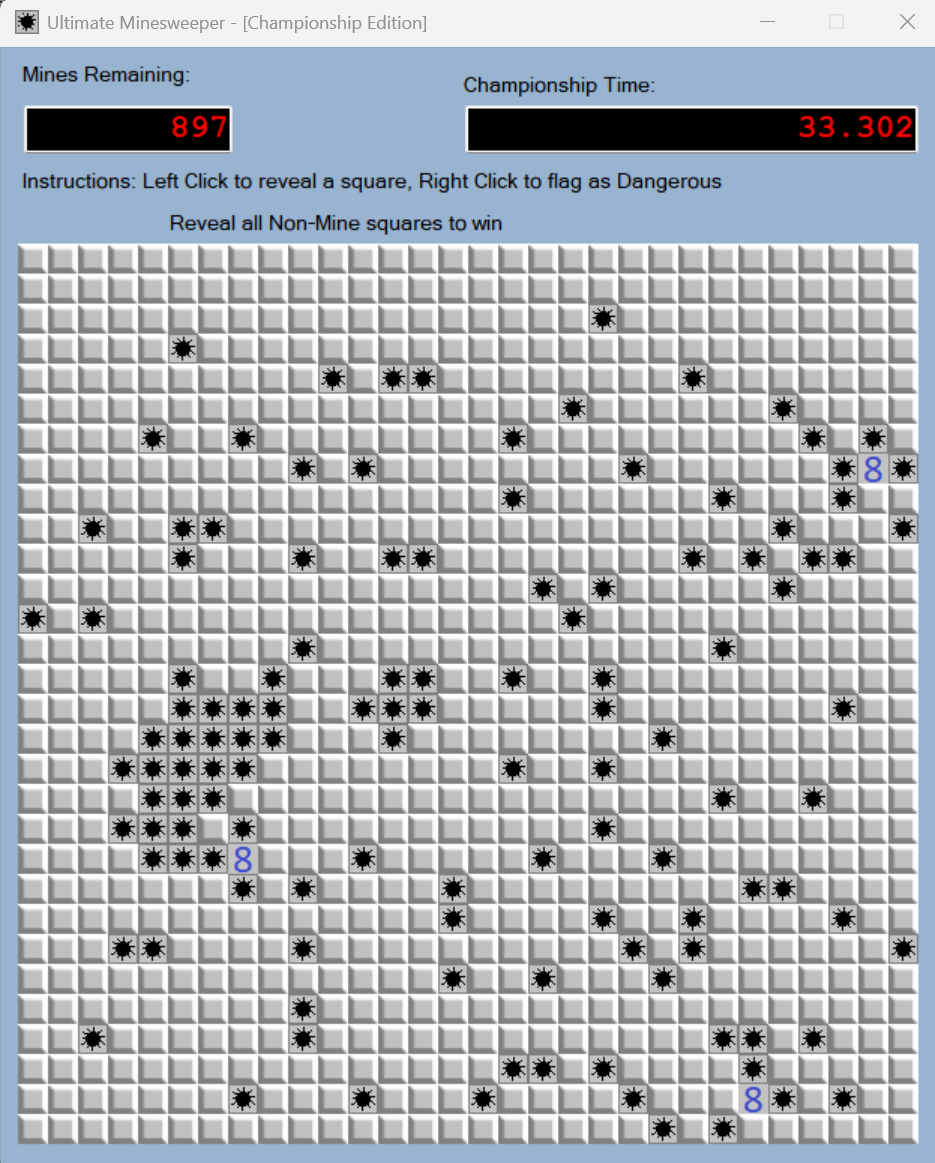
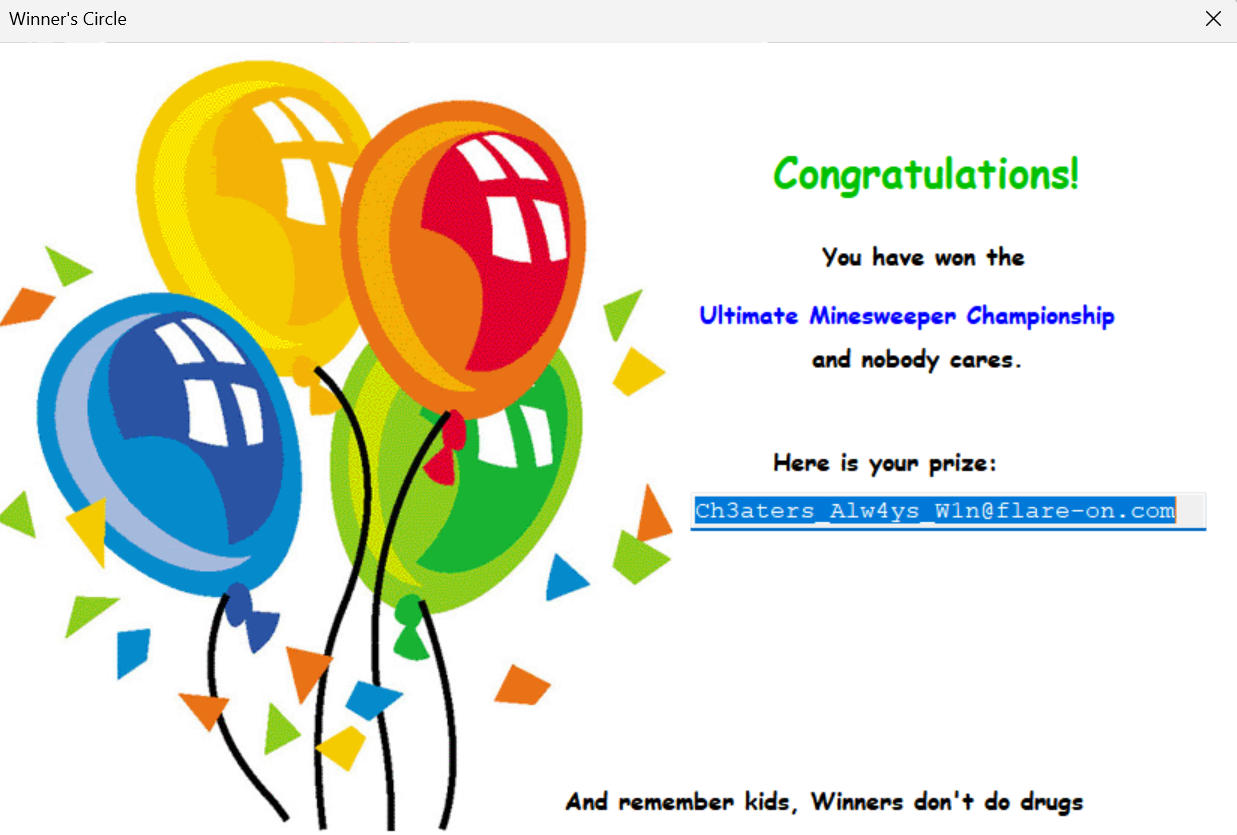
[FlareOn5] Ultimate MineSweeper
- 透视挂
- 无敌挂
- 提取数据
这题不会,但大佬三个方法中的一个,手动操作一下
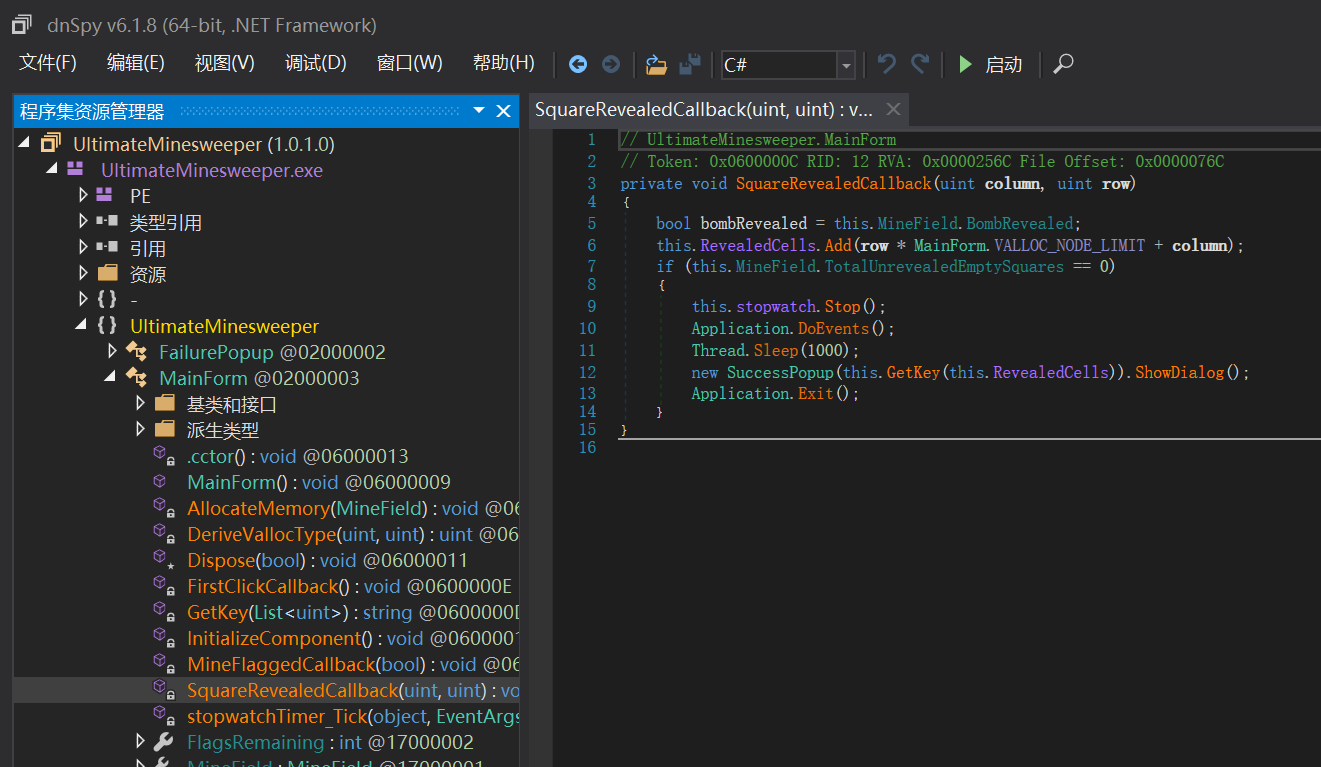
- 无敌挂
右键-编辑方法 或 ctrl+shift+E
改为 if (this.MineField.BombRevealed && false) 或直接把这段删除
1 | if (this.MineField.BombRevealed) |
变成这样
文件-保存模块,然后运行程序,找到旗子

[FlareOn4]login
- 题目是一个网页加密,直接查看页面源代码
1 |
|
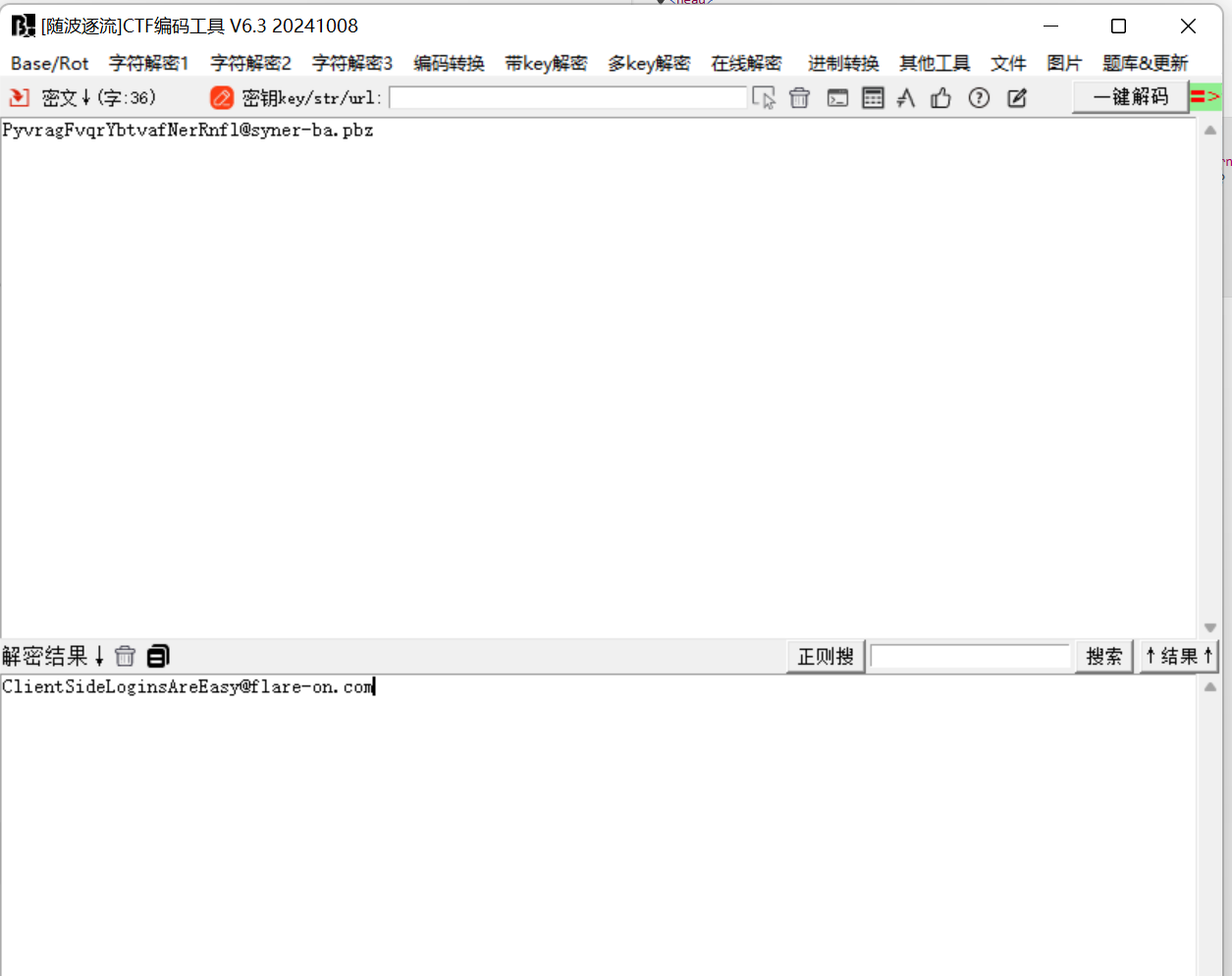
- rot13加密
1 | document.getElementById("prompt").onclick = function () { |
- rot13解密
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Elliot-Lin!